[ad_1]
Six telltale signs to know if you are experiencing a business email compromise attack. Additionally, we have included tips on how to protect yourself and your organization against BEC attacks
Editor’s Note: This is a guest blog contribution from Harman Singh, a security professional, director and managing consultant at Cyphere. Singh shares his perspective on how to identify common business email compromise communications and what organizations can do to fight this type of email fraud.
As the number of cyberattacks on businesses continues to rise, it’s clear that companies need to improve their security efforts. Cybercriminals are constantly developing new schemes to target businesses and those who do business with them. One such attack style, known as business email compromise (BEC), has been hitting organizations across all industries throughout the world. BEC attacks are particularly dangerous because they target businesses that are likely to have a lot of money available in their bank accounts (although any organization or individual can be a target).
In addition, the attackers often have detailed knowledge of the company’s structure and operations, which makes it difficult for employees to distinguish legitimate requests from fraudulent ones.
If we were to go by FBI’s IC3 2020 Internet Crime Report, BEC schemes are continuing to be the costliest. A total of 19,369 complaints incurred adjusted losses topping $1.8 billion. Yes, that’s around $2 billion of just known BEC scams… that doesn’t even count unreported crimes!
With all of this in mind, let’s explore how to recognize BEC scams and what you can do to protect your organization.
Let’s hash it out.
What Is Business Email Compromise? BEC Scams Explained
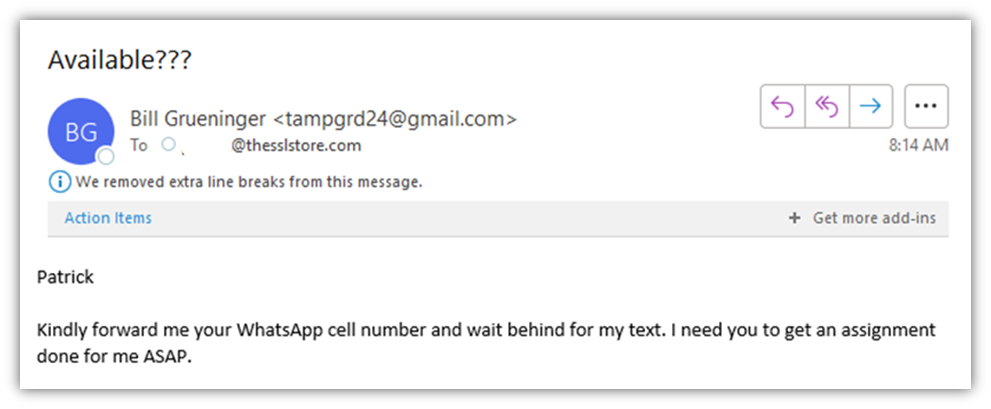
Business email compromise attacks are a type of phishing scam in which fraudsters try to hack, spoof or impersonate business email addresses. Social engineering is the central concept to the BEC attack preparation, where initial malicious actions are prompted by the victim using various social engineering techniques.
These attackers usually send emails to employees that appear to be from someone within the company, such as the CEO or another executive, or from a known third party (such as a vendor or partner). In some cases, an employee’s or executive’s email is hacked, and the attackers use the legitimate account to send invoice payments to vendors in their contacts list. (In other cases, they create similar-looking email addresses to trick their targets into thinking they’re authentic.) Payments are then sent to bank accounts controlled by the hackers.
BEC attacks made big headlines in 2020 when Shark Tank TV star and venture capitalist Barbara Corcoran almost lost $400,000 to this type of scam. Her bookkeeper was targeted by scammers impersonating Corcoran’s assistant. Thankfully, Corcoran was able to recover her money after she notified her bank and they froze the funds.
The goal of the attack is typically to convince the targeted employee to wire money to the attacker or to provide sensitive information, such as employees’ sensitive personal data.
An Overview of What Happens In a Business Email Compromise Scam
When threat actors plan attacks, a lot of behind-the-scenes preparation goes into setting up attack infrastructure and BEC attack strategy. Just like red teaming relies on the open source intelligence (OSINT) phase, a similar open-source information intelligence phase goes into the finding of the target staff, information available online and technologies/solutions used by the target.
BEC scams are often difficult to spot, as the attackers often have detailed knowledge of the company’s operations and hierarchy. They may know:
- Which employees are authorized to transfer money,
- What those employees’ email addresses are, and
- Which managers or executives they report to in their chain of command.
The attackers typically impersonate top executives to make the requests seem legitimate and to increase the urgency of the messages. They also use phishing attacks to get employees to click on dangerous links or open attachments that contain malware.
A Look at the Costs & Damages That Result from BEC Attacks
Business email compromise attacks involve a cybercriminal gaining access to a business email account and then using it to send fraudulent requests for money or sensitive information. These attacks can be costly and damaging to businesses, as the Ponemon Institute’s 2021 Cost of Data Breach Study found that the average cost of a data breach is $4.24 million.
When employees fall victim to a BEC scam and wire or send funds, the organization may be held liable for the damages. The company may also suffer damage to its brand and reputation if news of the scam goes public.
If customers learn that their business’s systems were attacked or compromised and their personally identifiable information (PII) was stolen, they may no longer trust the company with their data. This could lead to a loss of business and decreased revenue.
Okta’s The State of Digital Trust report refers to the same argument mentioned above where:
- Service reliability and good security policies were the two most important factors for consumers while considering a digital brand.
- 75% of U.S. consumers are likely to reject a digital brand when it comes to shopping based on trust.
If an organization’s email system is compromised, it may lead to disastrous impacts such as leakage of proprietary data, business secrets and compromise of PII. But there are plenty of other costs to be concerned about as well — paying for incident response tasks and teams, legal actions, and irreparable reputational damages.
Loss of compliance is another complexity while discussing the implication of a BEC attack, this could be loss of compliance with regulations such as the Health Insurance Portability and Accountability Act (HIPAA) or the Payment Card Industry Data Security Standard (PCI DSS). This may result in fines and other penalties.
3 Business Email Compromise (BEC) Examples
One of the most famous BEC scams of modern times caused $121 million against Facebook and Google. Evaldas Rimasauskas and his associates set up a fake company that used fake invoicing as a route to exploit employees’ trust. These two big tech giants lost millions to BEC attacks involving third party vendors over two years. This man was sentenced to five years in prison.
In 2019, a Toyota subsidiary lost $37 million in BEC attacks where attackers convinced an employee to transfer huge sums to a European subsidiary before they were identified.
The best way to protect your business from BEC scams is to be aware of the common tactics that attackers use. Here are a few example messages that attackers may use in their emails:
1. Request for an Urgent Wire Transfer
Dear Employee,
I hope this email finds you well. I am writing to request an urgent wire transfer. As you can see from the attached document, we have a client who is ready to make a payment for services rendered. Due to confidentiality reasons and company policies, I cannot provide an explanation of the nature of the transaction over email
Please review the attached files carefully and let me know if you have any questions or concerns. I would appreciate it if you could execute the wire transfer as soon as possible
Thank you for your time and cooperation
Sincerely,
CEO or another executive within the company
2. Phishing Attack Requesting Sensitive Information
Hello,
I hope this email finds you well. I am writing to request some sensitive information. As you can see from the attached document, we have a client who is ready to make a payment for services rendered
Due to confidentiality reasons and company policies, I cannot provide an explanation of the nature of the transaction over email
Please review the attached files carefully and let me know if you have any questions or concerns. I would appreciate it if you could send me the requested information as soon as possible
Thank you for your time and cooperation
Sincerely,
CEO or another executive within the company
3. Request for an Invoice Payment
Hello,
I hope this email finds you well. I am writing to inform you about an upcoming purchase order. As you can see from the attached document, we have a client who is ready to make a one-time purchase. Due to confidentiality reasons and company policies, I cannot provide an explanation of the nature of the transaction over email
Please review the attached files carefully and let me know if you have any questions or concerns. I would appreciate if you could process the transaction as soon as possible
Thank you for your time and cooperation
Sincerely,
CEO or another executive within the company
Business Email Compromise Warning Indicators to Look Out For
Simply put, common sense isn’t that common, and this sad reality is often exploited by scammers. The basic psychology at play during these attacks works by demonstrating and taking advantage of one of the following three factors:
- Situations where something is clearly required (your action) that are just too good to be true
- Exploiting the human desire that leads a person to trust the other party
- Curiosity-inducing contents and actions that result in more action, such as clicks and/or downloads
To protect your organization from future business email compromise attacks, look for the following warning signs:
- Emails that ask employees to wire money or purchase expensive items on behalf of the company.
- Emails that ask for sensitive information such as payroll information or W-2 forms, employee Social Security numbers, or company bank account information.
- Emails with misspelled words or poor grammar, as well as unexpected emails or emails in which the sender’s name is missing or unclear.
- Unexpected attachments sent by email.
- Emails sent after business hours or on weekends, holidays, or other nonstandard business days.
- Spoofed email addresses, as these are often used in BEC scams. Attackers will often use email addresses that are very similar to those of company executives.
How a BEC Attack Works
In a BEC attack, the scammer usually impersonates someone in a position of authority within the company. Many times, this person will appear to be the CEO or another executive.
The attacker may mention one-time passwords (OTPs) sent through SMS text messaging in order to convince employees that it’s a legitimate request. In addition, the emails often have a sense of urgency in order to pressure the employee into responding quickly. Sometimes, attackers pretend to be third-party vendors that request payments be made to fraudulent accounts.
The attacker may also use a spoofed email address so that it appears to be from someone within the company. This technique is a form of domain spoofing when the email sender’s domain is made to look legitimate.
The attackers often have detailed knowledge of the company’s operations, which makes it difficult for employees to distinguish legitimate requests from fraudulent ones. The email may contain information such as the name of the CEO and a fake copy of that person’s signature.
In some cases, the attacker may even know the names of specific employees within the company. This level of detail can make it tough for a business to tell who’s legitimate and who isn’t.
6 Ways to Protect Yourself Against BEC Exploits
There are several things that businesses can do to protect themselves against BEC attacks:
1. Educate Your Employees
One of the best ways to prevent a BEC attack is to educate your employees about the scam. They need to be aware of the signs of a scam email, such as messages that:
- Use poor grammar and spelling mistakes,
- Contain unsolicited links and attachments,
- Include sender information that doesn’t match the email address, and
- Convey a sense of urgency.
2. Enable Two-Factor Authentication for Email and Bank Accounts
Employees need to have two-factor authentication enabled when it comes to their business email account and bank accounts. Most commonly, this involves using a smartphone app such as Google Authenticator or Duo Mobile. In addition, employees should only open attachments from known senders.
3. Verify Communications Before Taking Action
When possible, employees should verify phone calls and emails before taking any requested actions. Regardless of whether it’s their boss or the company CEO, the best course of action would be to call them directly on their private lines or using a unique link included in an email.
Any requests to transfer money or sensitive information (such as usernames and passwords) should be verified. The best approach is to hang up the phone and then call the person back on their direct line.
Never respond to or click on links sent in suspicious emails.
4. Check Email Headers
The headers of an email message may contain information that can help you determine whether it’s legitimate or not. For example, the email may have an Internet Protocol (IP) address that’s different from the one normally used by your company.
5. Implement Email Security Measures to Protect Your Brand
Another security method you can put into action is setting up email security measures like sender policy framework (SPF), domainkeys identified mail (DKIM), and domain message authentication, reporting and conformance (DMARC).
- SPF allows you to set up a domain name system (DNS) record that specifies which IP addresses have authorization to send emails on behalf of your domain.
- DKIM adds a “signature” to your outbound email that lets your recipients’ email servers know that it’s authentic and legitimately came from your domain.
- DMARC uses both SPF and DKIM to its advantage to create greater email security. You can set up enforcement rules that require all inbound emails to undergo specific verification checks. If an email doesn’t meet certain standards, it will be rejected.
6. Install Malware Protection on All Devices
Your business should have malware protection installed on your devices to protect against malware and other cyber threats. This can include antivirus, anti-spyware or other types of protection.
What to Do If You’ve Responded to a BEC Email?
If you think you may have responded to a BEC email, there are a few things you can do:
1. Report it to your organization’s IT/cyber security team.
2. Contact your bank and ask to suspend all transactions.
3. Change your passwords for email and financial accounts.
4. Review your account statements for any suspicious activity.
5. Contact the police and file a report.
6. Contact your bank, credit card provider and financial institution to report the scam.
Have Concerns About Identity Theft?
If you suspect that you may be a victim of identity theft because of this attack, here’s what you can do:
- Contact one of the three national credit reporting companies (Equifax, Experian, and TransUnion) to place a fraud alert on your credit report, which will let creditors know that you may have been a victim of identity theft.
- Contact the Social Security Administration’s Office of the Inspector General to report any suspicious activity related to your Social Security number.
- Close compromised financial or credit card accounts.
- File an Identity Theft Affidavit with the Federal Trade Commission (FTC).
- Contact your state Attorney General’s office.
Final Thoughts on Business Email Compromise Scams
By understanding how BEC attack works and taking the necessary steps to protect yourself against them, you can help reduce your risk of being a victim. In this blog post, we’ve outlined various ways to keep your company safe from attack by business email compromise scams — whether it be through helping employees spot phony emails or through implementing policies that will ward off attackers.
If these tips have been helpful for you today, please share with other people who may need protection, too!
[ad_2]
Article link
