[ad_1]
Password compromises continue to be a leading security issue for organizations and their customers. 46% of Forbes’ U.S. OnePoll survey respondents say their passwords were breached in the past year.
There are many reasons why passwords can become compromised. Sometimes, it’s something as simple as hardcoding your credentials into applications. But in most cases, these situations occur as the result of various password cracking methods.
This is why today’s lesson will examine 9 password cracking attacks. We want you to understand these credential-compromising methods and what you can do to stop them.
Let’s hash it out.
A 30-Second Review: What Is a Password Cracking Attack?
Let’s start by quickly covering the basics (i.e., what a password cracking attack is) before moving on to the specific techniques. In a nutshell, password cracking is a way for someone to gain unauthorized access to a password.
Of course, many methods and techniques can be used to achieve this goal. But when drilling right down to the heart of the issue, password-cracking attacks target either the technical or non-technical vulnerabilities (or both) that exist within your organization’s IT ecosystem.
What Are the 4 Categories of Password Cracking?
Of course, industry professionals have different ideas about what constitutes password cracking. But we’ll run with Michael Solomon’s and Sean-Philip Oriyano’s definition for the sake of this article.
In their book “Ethical Hacking: Techniques, Tools, and Countermeasures (4th Edition)” Solomon and Oriyano identify four overarching categories of password cracking methods:
- Active online attacks — These attacks involve threat actors taking deliberate actions, such as by using massive lists of guessed username-password combinations to force their way into legitimate accounts.
- Passive online attacks — Examples of these types of attacks include man-in-the-middle (MitM) attacks and packet sniffing. Basically, this more laid-back approach takes advantage of someone’s insecure connections and vulnerable technologies.
- Offline attacks — These attacks don’t require intercepting data in transit or poor choices of passwords. They instead focus on the security mechanisms relating to how and in what formats the passwords are stored.
- Non-technical attacks — These methods involve exploiting your employees’ and other users’ lack of cyber awareness and bad password security practices (e.g., their choice to use weak or recycled passwords).
Basically, these attacks focus on the security mechanisms you use to protect passwords and the humans you have working within your network and other IT environments. They exploit vulnerabilities that exist within your authentication systems, server configurations, and employees’ security practices.
9 Common Password Cracking Methods That Can Harm Your Business
Alright, it’s time to start exploring some of the most popular password cracking techniques and mechanisms bad guys love to use. For this article, we’ve divided these password cracking methods based on what the attacker does and what (or whom) they target.
Taking Advantage of Employees’ Human Nature
I hate to break the news… but like you and me, your employees are human. Humans make mistakes. Sometimes, these mistakes include using weak passwords that are easy to guess. In other situations, they may be tricked or manipulated into sharing their secrets.
No one is infallible. For example, you or a colleague might accidentally misconfigure your password database, leaving the secrets within vulnerable. Although a security misconfiguration isn’t an example of password cracking specifically, it just shows that even IT professionals aren’t infallible. And if the pros make mistakes, then it can be expected that less tech- and security-savvy employees will as well.
But rather than pointing fingers, our point here is that these types of human error-based mistakes result in handing bad guys your now-compromised credentials on a silver platter. Regardless of how a password compromise occurs, the bottom line is that these issues frequently stem from human-related vulnerabilities, and all it takes is one “oops” for your day to go from good to bad.
Verizon’s 2023 DBIR data indicates that 74% of data breaches involved the human element. Knowing this, it’s time to explore four of the ways that bad guys love to exploit human-based vulnerabilities.
1. Phishing Attacks and Social Engineering
First on our list of password cracking methods is phishing. A phishing attack typically involves bad guys sending fraudulent emails, setting up fake websites, or even making phony phone and video calls to achieve their goals. Even generative AI tools can play a role in carrying out these scams!
In some cases, cybercriminals will go the extra mile by pairing these outreach methods with social engineering tactics. The goal? To exploit human emotions, fears, and responses to seemingly urgent situations. They’ll often create fake emergencies or urgent situations to trick or manipulate an employee into doing their bidding (e.g., sharing their passwords).
Here’s an example of a phishing scam in which an attacker impersonates Microsoft and pretends that my colleague has been charged for software he didn’t buy:
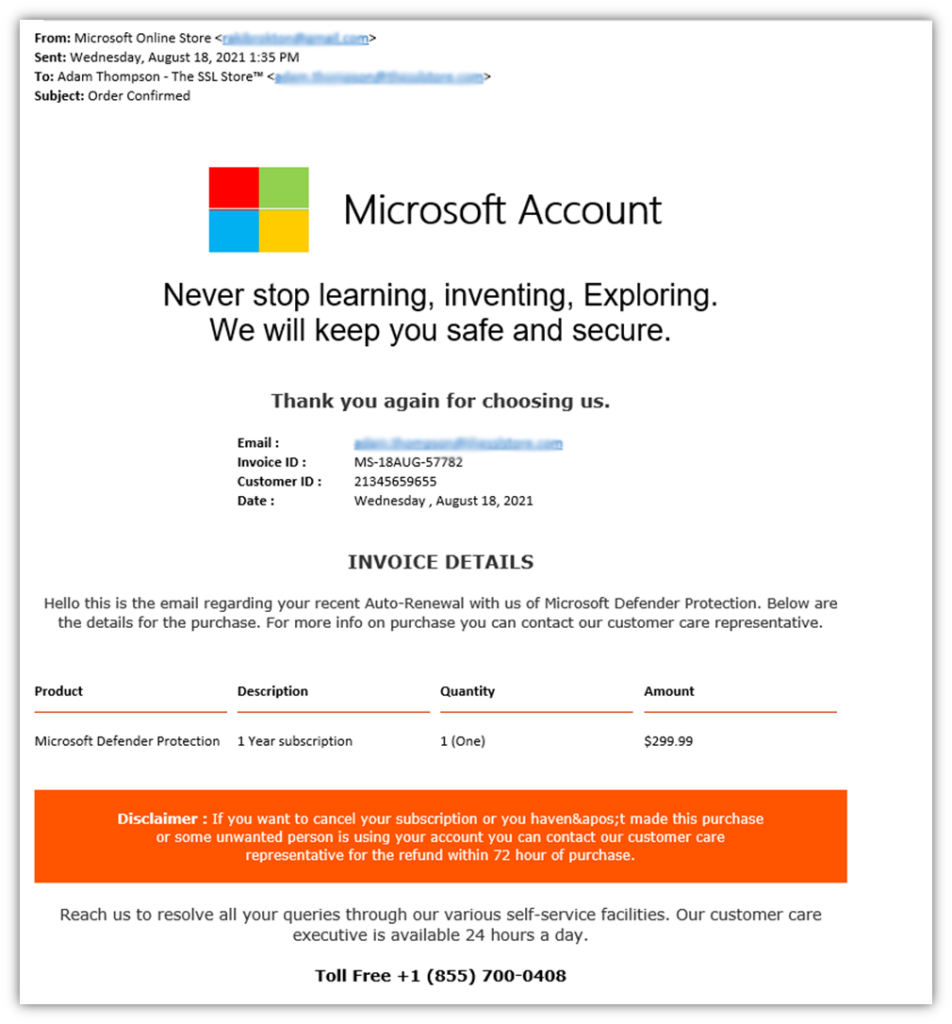
Furthermore, researching their target helps the attacker make more informed guesses about possible passwords that the person may use. For example, passwords that include the names or birthdates of children, pets’ names, and important dates such as anniversaries will be easier for a bad guy to guess.
2. Brute Force Attacks
The name alone pretty much tells you what you need to know. A brute force attack is a password cracking method that involves a bad guy trying to force their way into legitimate accounts by guessing combinations of usernames and passwords until they find a successful match.
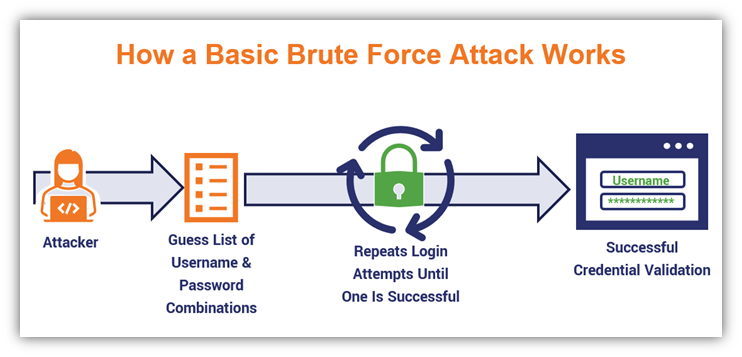
It’s important to note here that “brute force” is both a category of password attack as well as a specific attack method. (Not too confusing, right?) Although this and the following two items on the list technically fall within the category of brute force attacks, I’m separating them as individual types of password cracking attacks because bad guys go about carrying them out in different ways.
If an attacker takes the time to research the company and discover any password-related rules, it helps to narrow down the number of choices they’d have to guess. For example, if you know a company requires a password between 8 and 12 characters, and only certain special characters are allowed, then that narrows down the pool significantly.
3. Credential Stuffing Attacks
Similar to brute force attacks, credential stuffing attacks also involve an attacker using a long list of username and password combinations. However, in this case, the attacker has a list of previously compromised credentials they use botnets to try out on various web apps until they get a hit.
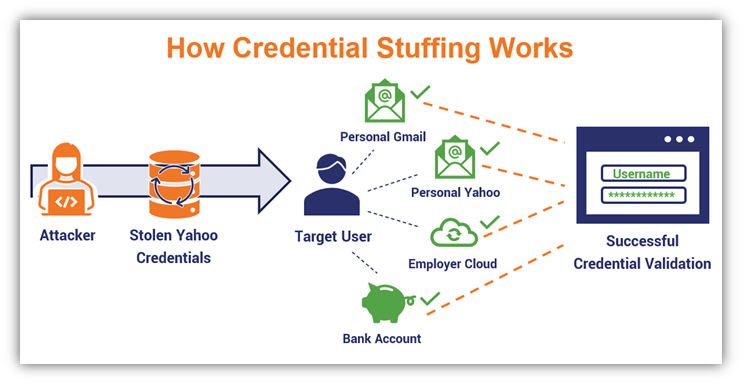
This approach typically involves using lists of usernames and passwords that have been leaked or stolen in previous data breaches. Cybercriminals frequently sell, barter, and share compromised credentials on the dark web. They also use information about the target to help calculate and guess additional passwords.
This underscores the importance of ensuring that employees get into the habit of changing their usernames and passwords whenever there’s a breach. Be sure to remind them to use new, unique passwords and not reuse old ones from other accounts…
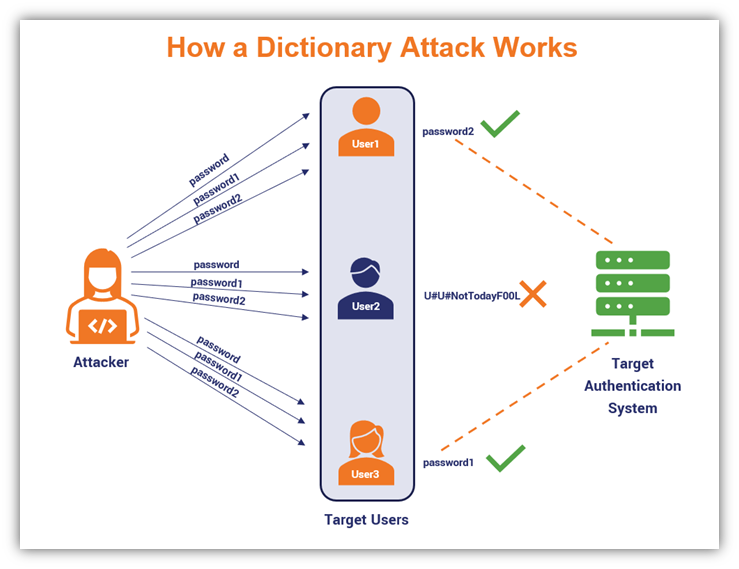
4. Dictionary Attacks
This type of password-focused attack involves using a massive, predefined list of common words that you can find in a dictionary. An attacker then builds upon this list to create as many permutations as possible, often using password cracking tools that help simplify or speed up the task.
Using Password Cracking Tools and Services
It’s no secret that threat actors often love malicious scripts and malware. For example, some use keyloggers to get their grubby hands on users’ credentials. But those aren’t the only types of tools that are useful for achieving the end result of snagging passwords…
5. Password-Cracking Software
Password cracking software is an application that’s used to crack passwords. Some are application- or file-specific, and virtually none are the instant fixes that movies and TV shows make them out to be. These tools aren’t instantaneous and require preparations to be made in terms of creating the password lists that an attacker will use.
Examples of popular password cracking tools and services include Aircrack-ng, RainbowCrack, John the Ripper, and Ophcrack.
Now, we’re not here to provide a tutorial for bad guys. However, these tools do serve legitimate uses for organizations’ cyber security teams (we’ll speak more about that later).
6. Packet Sniffing Tools
Packet sniffing solutions are useful tools for cybersecurity experts. They enable attackers to eavesdrop on communications, much like a man-in-the-middle (MitM) situation, but it’s more passive than active.
When used by ethical hackers and IT teams, they can be useful in helping to identify vulnerable traffic. But when used in the wrong hands, these tools can be used to do the same tasks (e.g., network and traffic monitoring) for different purposes and much uglier outcomes.
A packet sniffer can be used to detect and capture passwords as they move between two devices on a network. Examples of popular packet sniffing tools include the opensource packet analyzer tools Wireshark and tcpdump.
Just keep in mind, however, that packet-sniffing tools can sniff data on HTTPS connections. But if the attacker doesn’t have access to the private key that’s required to decrypt the secure data, all the attacker will see is a bunch of gibberish.
And now for a bit of shameless self-promotion… This type of situation serves as a great opportunity to remind you to always use a valid SSL/TLS certificate on your website to maintain secure, encrypted connections. To do this, be sure to manage your certificates and keys securely!
Exploiting Bad Password Storage Practices
Employees and customers aren’t the only ones with bad habits… in some cases, password security breaches stem from companies not properly securing passwords or their hash digests from a technical perspective.
7. Exploiting Stored Plaintext Passwords
Bad guys love simplicity. The easier a target is, the least amount of effort it requires and the bigger the pay day in terms of what they’re getting in contrast to the energy and time expended.
Knowing this, let’s say the following loud enough for your momma in another state to hear:
- Never store plaintext passwords in your database. If you upload plaintext passwords to a database, and that database becomes compromised, then you’re in for a world of pain.
- Avoid storing plaintext passwords in configuration files. Storing plaintext passwords in a properties file isn’t a good approach, either.Along the same lines as storing plaintext passwords in a database (although, maybe, ever so slightly better), it leaves your passwords vulnerable to access by anyone with authorization. This means if an authorized employee’s access is compromised, then so is everything in any system or file they have access to through that legitimate account.
This is why it’s crucial for businesses to store (salted) password hash values instead. Hash digests are the output values that result when you apply a cryptographic hashing algorithm to your password inputs.
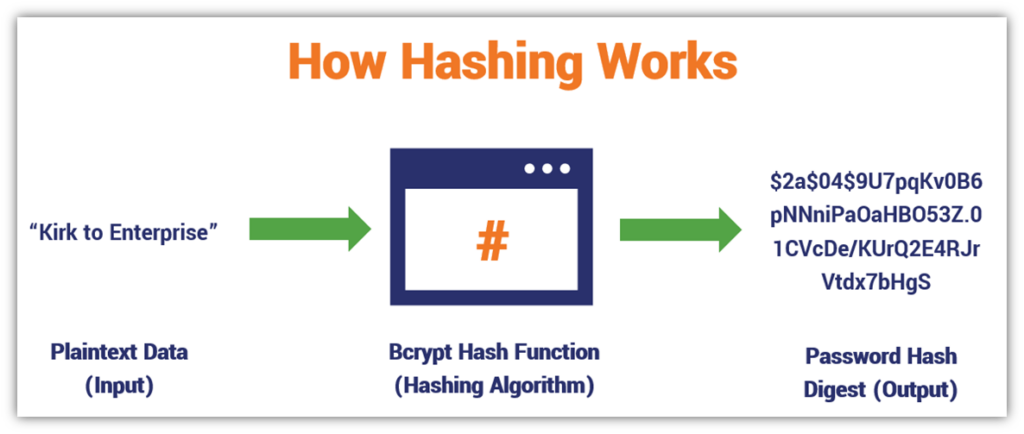
For better security, though, it’s imperative to salt your passwords. That’s because hashing is deterministic, meaning that you’ll always get the same output when you hash an input. So, if User A and User B are both using “CaptainKirk” as their password, they’ll end up with the same hash digest.
By making any change to the password prior to hashing, no matter how small, you’ll get an entirely different hash value output.
This is why salting your passwords before hashing is important. A salt is a unique, random value that’s generated using a random number generator (RNG). By adding a salt, even if two people use the same password, they’ll have unique salts added to their passwords that result in unique hash value outputs once hashed.
8. Hash Table Attacks
This password cracking method involves an attacker calculating a table listing the hash values of all possible passwords matching certain parameters when hashed using a specific hash function.
As you can imagine, this approach requires an immense amount of time and data storage. However, it enables bad guys to compare and contrast hash values they come across in breaches and gives them a list of passwords to run in brute force attacks.
As you’ve learned, simply hashing your passwords and storing the hash digests isn’t enough; you have to take things a step further by adding a salt to protect against the next type of password cracking attack method…
9. Rainbow Table Attacks
A rainbow table attack is another way for bad guys to figure out how to crack unsalted, hashed password values to determine the original password input. However, it’s a different approach from traditional hash tables, and is better for trying to crack more complex passwords.
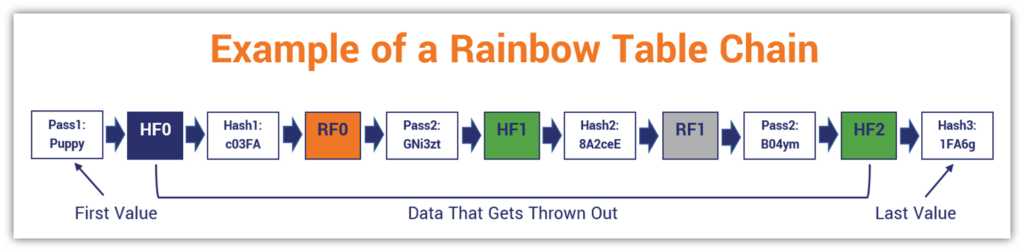
To do this, rainbow table attackers create massive password-hash chains comprised of one-way hash functions and hash reduction functions. However, they only store the bookend information (i.e., the first and last values of chain data), which can be used to regenerate the chain data when needed at a later time.
This is why it’s important to not only store hash values in place of plaintext passwords, but to add salts to those inputs first before hashing them. This way, you only store the salted password hash values, combatting rainbow table attackers.
Just How Big of a Threat Is Password Cracking?

Data from Proofpoint’s 2024 State of the Phish Report indicates that users’ habitual use of bad password security practices and misconceptions is a big issue.
- Seven in 10 working adults admit that they take risky actions (96% say they did so knowingly).
- 26% indicate that they reuse or share their passwords.
- 59% of users either denied or weren’t sure whether they were responsible for security within their organizations in any way.
Among the top five riskiest behaviors demonstrated, reusing and sharing passwords ranked as the second most common risky action taken by survey respondents.
How to Mitigate Password Cracking Attack Risks and Threats
Cybercriminals have many tools in their password cracking arsenals. But this isn’t a one-sided fight; there are things you can do to fight back and prevent bad guys from winning the day.
1. Educate Your Employees to Improve Their Password Security Practices
Your employees are your most pivotal line of defense. If attackers can sweet-talk, threaten, trick, or manipulate your employees into handing over their passwords, then it’s virtually game over as far as your security is concerned.
2021 data from Norton shows that 57% of users will retroactively make their account passwords stronger after detecting unauthorized access. However, that doesn’t help prevent attackers from compromising their accounts in the first place. Your network users should be using more secure passwords (or passphrases) from the get-go.
If a bad guy is able to guess your employees’ credentials or brute force their way into their accounts, then they have access to anything the employees’ now-compromised user profiles provide access to. This could be everything from your intellectual property and development environments to payroll and other finance accounts.
This is why it’s critical to teach your employees about common password security-related threats and to practice the following:
- Use strong, unique passphrases instead of passwords. This entails typically using a complex password (or, ideally, a passphrase) that’s at least 12 characters long. (The late Kevin Mitnick, one of the world’s leading hackers, recommended passphrases should be at least 25 characters. While it might sound like an inordinately long secret, it can be easy to remember if done well!)
- Avoid sharing passwords with other employees. This is a major no-no that we often see in companies. We get it — setting up individual accounts can be expensive and cumbersome. But you know what’s more so? Dealing with the consequences of a data breach.
- Ensure their passwords and other secrets are stored securely. Passwords are only useful if they remain secret. If you’re writing down your passwords and posting them out in the open, then it’s only a matter of time before the wrong person sees them and decides to use ‘em to their advantage.
- Be security-conscious when entering passwords. It’s crucial for employees to practice situational awareness, especially when typing in login credentials when working in the office and remotely. Just as someone should ensure no one is looking over their shoulder when entering a debit card PIN at an ATM, employees should take the time to look around and be aware of where people are when logging into their accounts.
There’s not much you can do to stop a cybercriminal from using an employee’s legitimate login credentials if you don’t know they’re compromised. But this is where our next password cracking attack mitigation method comes into play…
2. Create a Culture of Accountability and Honesty (Not Fear)
In cyber security, one of your organization’s greatest enemies is an employee’s fear of making mistakes and facing the consequences that follow. If an employee is too afraid to report a security issue or mistake for fear of the consequences, they might choose to keep it secret.
Consider that Proofpoint’s report data indicates that only 18.3% of simulated phishing emails received by users in 2023 were properly reported. (The simulated emails had an average failure rate of 9.3%.) Now, imagine what would happen if your employees received a real phishing email:
- How many would open it and click on a link?
- How many employees would be tricked into typing in their passwords?
- How many would tell you that they did?
Require Everyone to Report Security-Related Incidents
Whether an employee falls for a phishing email or shares their password with a scammer over the phone, they need to know that they must change all account passwords immediately. They also should know:
- That it’s their duty to report all cyber security incidents immediately;
- What the processes and protocols are for reporting security situations to your organization’s SOC or IT team; and
- The sooner they report an issue, the faster it can be addressed (and potential damages minimized).
Proofpoint’s 2024 data shows there’s a disconnect between what security pros and their users think in terms of security responsibility within an organization. 85% of security professionals were confident that “most employees know they are responsible for security,” but this flies in the face of nearly 60% of users who claimed otherwise (i.e., that they’re “not responsible at all” or aren’t sure whether they’re responsible.
3. Implement Strong Password Storage and Security Practices
Your employees can have the perfect passwords, but if you don’t store them securely, then their diligence in creating unique, secure passwords won’t matter. Their accounts will be compromised and your customers’ trust in your organization will take a hit.
To make all users’ passwords as secure as possible:
Remember: Passwords are only as secure as the methods you use to protect them. If you implement the necessary protections up front, you can avoid many of the heads that would otherwise result later.
4. Add Layers to Your Authentication Security
In addition to the methods we’ve already covered, there are additional steps that your IT admin and network security teams can take to make accounts more secure.
- Implement multi-factor authentication (MFA), if available, or single sign-on (SSO).
- Set up login limits that lock users out of accounts after X number of failed sign-ins.
- Use generic failed login response messages. Don’t specify whether a password or username is incorrect. (Don’t give attackers any extra information they can use to make their dastardly jobs easier.)
- Use CAPTCHAs or similar verification methods (e.g., Cloudflare Turnstile) to help fight bots.
Related Resource: Compromised Credentials: 7 Ways to Fight Credential Attacks
Alternatively: Use PKI Authentication to Avoid Password-Related Risks Outright
Ditch the traditional passwords and use certificate-based authentication instead to secure access to your network’s resources and company accounts. Using a client authentication certificate enables your employees to authenticate to authorized systems without the usual password-related risks.
By making passwords superfluous in favor of PKI-based authentication, this helps you to avoid:
- Complacent employees reusing passwords to secure multiple accounts
- Employees writing down passwords and storing passwords insecurely (e.g., recording their passwords on sticky notes on their desks)
- Passwords being stolen via social engineering and man-in-the-middle attacks (when paired with HTTPS encryption)
Password cracking tools have applications as exploitation analysis tools. Some organizations’ IT security teams use password cracker tools as pentesting tools to test the strength of their employees’ passwords and identity vulnerabilities. They also might use phishing simulation tests to identify the weak links in your cyber defense armor.
And while using password cracking tools and methods aren’t necessarily illegal in certain use cases (e.g., when you’re using it for data and accounts you have authorization to use), it’s still something you need to do with an abundance of caution.
If you decide to use these approaches within your own environment, especially when using password cracking tools, just be sure to run the idea up the flagpole first for approval (i.e., get the sign-off from leadership). While your intentions are good (i.e., trying to mitigate password-related vulnerabilities), management may not view the situation the same way and you could find yourself in hot water.
TL;DR: Key Takeaways About Preventing Password Cracking Attacks
So, what are some of the key takeaways we learned from this article?
- Proofpoint data indicates that one in four survey recipients say their users reuse or share their passwords.
- 71% of working adults admit to risky behaviors (96% of Proofpoint survey respondents say they engaged in these activities knowingly!)
- Bad guys aren’t afraid to exploit vulnerabilities that exist in your human firewall or technical defenses.
- Password cracking isn’t just software; it also includes non-technical approaches (e.g., phishing and social engineering), too.
- Password cracking protection starts with individual cyber security awareness and strong passphrases or the use of PKI-based authentication.
- Not all password cracking is inherently bad — when used for legitimate purposes, password cracking tools and tactics can improve your organization’s cyber security by identifying potential exploits.
As you’ve learned password cracking can be used for good or evil purposes. From IT security and pentesting perspectives, these tactics and tools are vital for rooting out vulnerabilities — ideally before attackers have a chance to exploit them — to improve their organizations’ cybersecurity.
[ad_2]
Article link
