[ad_1]
Indicators of compromise (IoCs) are the digital “clues” cybersecurity professionals use to identify system compromises and fight back against cybercriminals. Understanding how to identify and use IoCs in cybersecurity can be the difference between falling prey to an attack and motivating attackers to look elsewhere for an easier target
Earlier this year, the Federal Bureau of Investigation (FBI) released a report on the Zeppelin ransomware variant. Part of this joint advisory was a discussion about the attack techniques used by these ransomware actors and key pieces of data called indicators of compromise. In this case, those indicators (i.e., markers) were hash digests associated with malware used in ransomware attacks against critical infrastructure organizations.
But what are cybersecurity indicators of compromise? How can we use them to find existing compromises and strengthen our cyber defenses against future attacks? This article is the first in a two-part series on IoCs in cybersecurity and how you can deploy them to shut down future attacks.
Let’s hash it out.
IoC Cybersecurity: What Are Indicators of Compromise?
(Looking for the quick-and-dirty takeaways on cybersecurity indicators of compromise? Just jump to the end of the article — we’ll provide you with a quick overview of what you need to know.)
Indicators of compromise are the digital trace evidence showing that a potential intrusion or compromise has occurred (typically on your host system or network) previously. This evidence includes (but isn’t limited to) the tactics, techniques, and procedures (TTPs) cybercriminals used to gain the access and control they desire within your environment. Once inside your network, they can then pivot — moving from one system to the next, accessing and exfiltrating data as they please.
Essentially, these markers are the big red flags that say, “something went wrong and here are some clues as to how it occurred!” They help you identify ongoing compromises of your system. However, IoCs are more than just gathered evidence of past security events and current compromises — they’re also data you can apply to your cyber defenses to help prevent stop future attacks.
When we think about cybersecurity as an industry, it’s all about preventing data compromise and unauthorized access to your systems. Basically, it’s all about keeping your organization from becoming the next cybercrime statistic. A key part of fighting the good fight against cybercrime and cybercriminals involves understanding who the attackers are and how they work.
Indicators of compromise are, essentially, like finding your enemy’s playbook and attack plans: You can study their approaches and techniques to better prepare you for future engagements in this ongoing digital war against cybercriminals.
The Cybersecurity and Infrastructure Security Agency (CISA) has a great webinar that talks about indicators of compromise for incident response more in depth:
So, with all of this in mind, what are some specific examples of cybersecurity IoCs?
A Quick Look at Common Indicators of Compromise
Indicators of compromise can be fairly obvious, or they can be more subtle in nature where you might miss them if you’re not paying attention. Some common indicators of compromise include:
- Phishing or malicious emails being sent from your domain
- Your domain takes a reputation hit for being reported as sending spam
- Discovering known malicious files on your devices or network
- Slow network connections
- Large amounts of outbound traffic on your network
- Inbound traffic from unusual or high-risk geographic locations
- Unusual traffic on privileged user accounts
- Account or access-related issues
- New account creation outside normal business hours
- Unknown or unauthorized system configuration changes
- System or data corruption
- Data breaches or compromises of third-party software or service providers you use
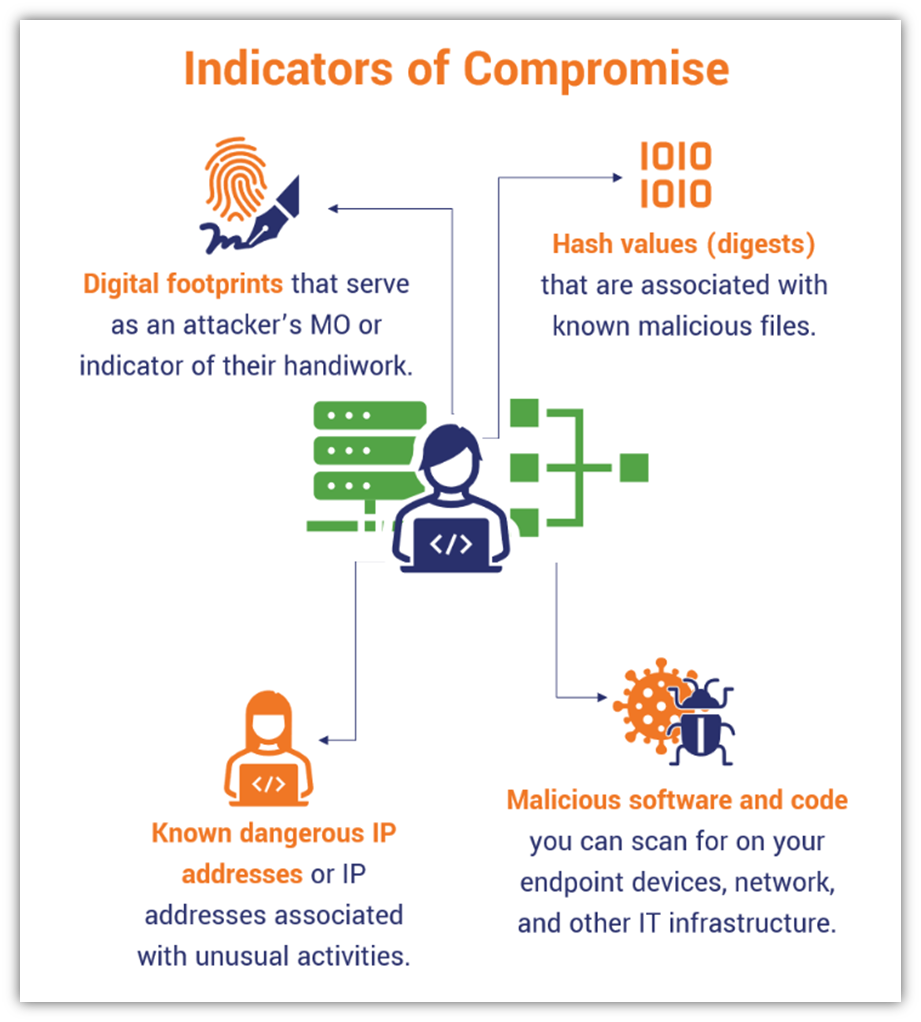
Drilling down on this a bit more, a few specific examples include:
- IP addresses
- Digital footprints or identifiers that give a clue about the attacker’s identity or method
- Tools used
- Malicious code injections or software programs
- Hash digests (i.e., fixed-length strings of hexadecimal characters) associated with known threats
- URLs and domain names
Why They Matter: Indicators of Compromise Are Tell-Tale Signs of Unauthorized Access
A simpler way to think of indicators of compromise is like they’re the breadcrumbs or clues a detective uses to figure out whether someone wrongly gained access to your home. They’re like the digital equivalent of physical indicators you’d commonly see in a home invasion scenario, such as:
- Scratch marks or scuffs around your door’s keyhole
- Dig marks, indentations, or other damage to the door or doorframe
- Malfunctioning door or window locks
- Fingerprints or shoeprints from the crime scene
Furthermore, depending on how they carry out their attack — the methods and techniques they use, the way they write code, etc. — also provides insights about the attackers themselves. Attackers often have some kind of modus operandi (MO), or a signature of some kind (intentional or otherwise), that can shed light on their identities.
All of this essential data plays a pivotal role in informing your cybersecurity decisions and approaches. You can use this information, in addition to automation, to prioritize and respond to identified threats within your environment.
What Indicators of Compromise Tell You About a Security Incident
Obviously, IoCs tell you that your system has been compromised and that you need to get the intruder out ASAP. But they also offer other key insights about both the attackers and the attacks they carry out. They tell you:
- Who was responsible for the attacks (i.e., who your threat actors were)
- What occurred (how your system was compromised)
- When your system was compromised
- How severe the incident was (i.e., how much damage, if any, was done)
- Where you need to focus your response and mitigation efforts
These cover nearly all of the 6 “Ws and an H” we talk about in journalism — who, what, when, where, why, and how — but you may notice an important one is missing from the list above: why. Unfortunately, IoCs don’t convey any information about motivations (unless the threat actor decides to write you a note or otherwise communicates their reason[s] for their actions — such as leaving a note stating that they’re doing something for a political or social cause). But in many cases, the “why” is fairly obvious once you know the “who.”
Not All Cybersecurity IoCs are Created Equally
Some indicators of compromise hold more weight than others when it comes to their importance and usefulness in strengthening your cyber defenses. Cybersecurity expert David Bianco came up with a way to classify IoCs in terms of the amount of “pain” they create for attackers when you effectively block their use. In Bianco’s own words:
“This simple diagram shows the relationship between the types of indicators you might use to detect an adversary’s activities and how much pain it will cause them when you are able to deny those indicators to them.”
Some indicators of compromise are easier than others for cybercriminals to change. For example, it’s relatively easy to process to change your IP address via proxy services. Others, however, like TTPs are a lot more challenging and costly to change. Therefore, they’re considered more reliable in terms of IoCs to deploy as part of your cyber strategy.
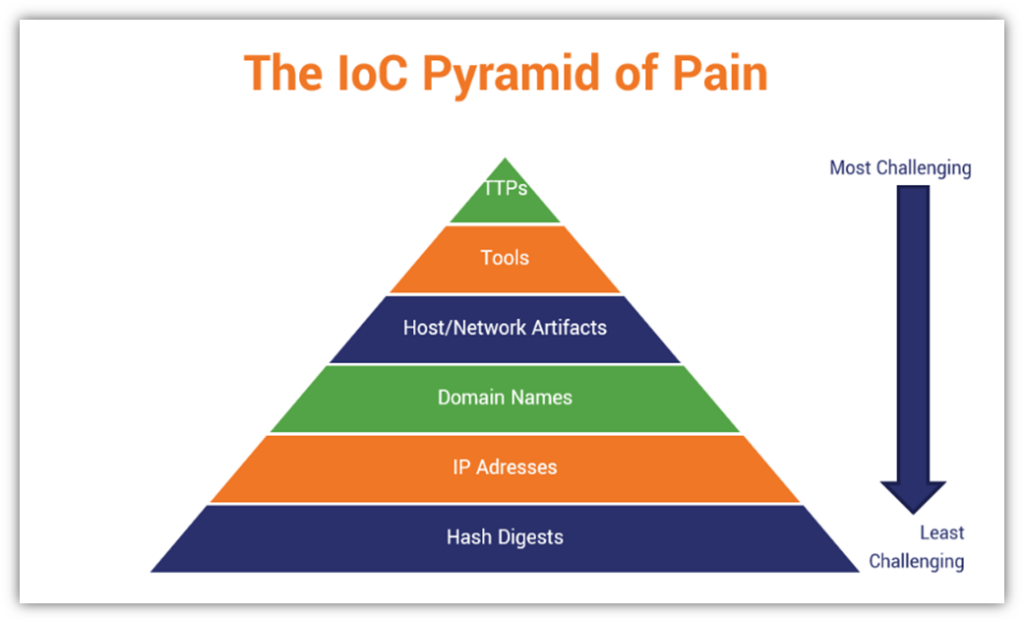
Here’s a quick overview of each of these elements of the pain pyramid, moving from most to least costly and complicated to change (and best to target for enhanced cybersecurity):
- TTPs — These are the most effective things to focus on because they’re also the most complex and costly things for cybercriminals to change. TTPs involve everything from reconnaissance and methods to everything in between — basically, everything they need to do their dastardly deeds. So, by targeting these specific behaviors and indicators, you’re using actionable threat intelligence to your advantage to help identify and stop current compromises and to prevent or mitigate future attacks.
- Tools — Creating proprietary scripts, utilities, and other tools and learning how to use them takes time and resources for bad guys to do. Therefore, targeting these specific indicators is useful for many of the same reasons as TTPs because you’ll now know what to look out for to prevent and mitigate current and future compromises of your IT systems.
- Host/Network Artifacts — If you can identify specific artifacts (i.e., elements that are unique to the attacker or attack, such as an attacker’s coding pattern or style), you can use that information to block requests that include them. While this won’t stop an attacker for good, it’ll make it so that they have to figure out how you identified them and make changes to stop you from doing so again.
- Domain Names — Though not impossible, changing your domain isn’t as easy as, say, changing your IP address as an attacker because there are more tasks and costs involved. So, slightly more complicated but not enough to put the kibosh on the plans of a determined attacker.
- IP Addresses — This is some of the lowest hanging fruit when it comes to indicators you can set your automated tools to watch out for. IP addresses aren’t challenging for attackers to change, which means that simply blocking these won’t stop a determined attacker by any stretch. However, blocking known or suspected malicious IP addresses can block automated attacks that don’t involve proxies or other IP masking or altering tactics.
- Hash Digests — The unique hash values of suspected (or known) malicious files are easy enough to target and also for bad guys to change. So, yes, keep an eye out for them and set your detection technologies to detect them, but keep in mind that these hash values may change as attackers want to stay at least one step ahead of you and your scanning tools.
Indicators of Compromise (IoCs) vs Indicators of Attacks (IoAs)
Unfortunately, there’s a little confusion when it comes to differentiating IoCs from indicators of attacks. This is because some people use the terms interchangeably (kind of like how people refer to TLS as SSL even though they’re two related but separate protocols that work differently at the nitty-gritty, technical level.) Simply put, IoCs are after-the-fact data, which differs from indicator of attack (IoA) data that aims to help you identify and respond to threats in real time.
- Indicators of compromise are about getting useful information about an attack after it happens so you can put an end to an ongoing compromise and, ideally, identify future attacks or breaches when they occur via enhanced detection and response processes. (Fool me once, shame on you. Fool me twice, shame on me.)
- Indicators of attack are all about identifying attacks as they’re happening to stop them from occurring. The idea here is that you can stop the attackers in their tracks — ideally, before they have a chance to compromise your system.
What to Do With IoCs Within Your IT Environment
Cybersecurity pros use IoCs in cybersecurity to detect and identify malicious activities and advanced persistent threats (APTs) within your network or IT environment. Why? So they can respond to events and threats to mitigate them. Basically, these giveaways play a key role in helping the “good guys” block the “bad guys” who want to access your sensitive data and systems.
Staying up to date on the latest indicators of compromise and understanding how they work helps you:
- Detect and identify attacks on your network or other IT assets as quickly as possible
- Test the effectiveness of your cyber defenses
- Identify and mitigate vulnerabilities that bad guys can exploit
- Improve your analysis and training capabilities using real world examples
- Strengthen your cyber defenses to make yourself a tougher target (i.e., prevent attacks from occurring in the first place)
How You Can Put IoCs to Work Within Your Environment to Prepare For Future Attacks
Let’s take a quick look at the indicators of compromise life cycle:
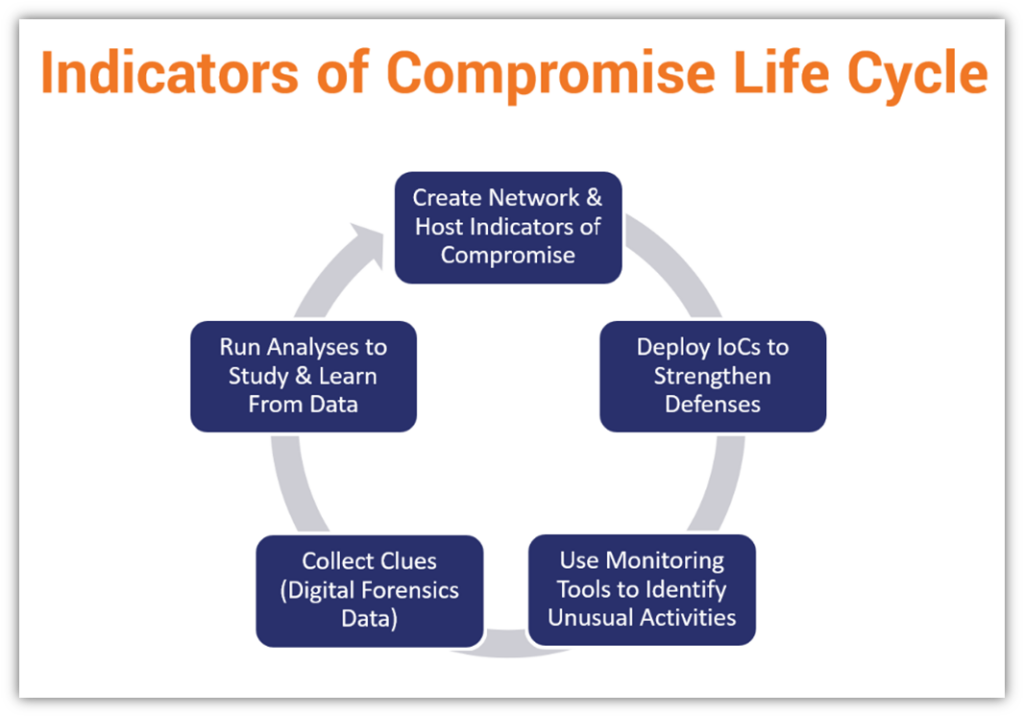
IT security teams should stay abreast of industry resources and news relating to new indicators of compromise. These types of information often can be found in case studies, research reports, vulnerability databases, and authoritative resources (such as the FBI’s Cybersecurity Division). When you do this, you’ll learn about all sorts of new and ongoing indicators of compromise you can apply within your own organization.
- Create a list of network and host indicators of compromise. These are the key pieces of data or traits that you want to look out for to identify compromises of your systems or data. One such example is unauthorized changes to settings or detecting unusually large numbers of requests for individual files.
- Deploy IoC detections to strengthen defenses. You can set your various threat detection, monitoring, and response solutions to look for and alert you to identified or potential threats based on the IoC information.
- Use monitoring tools and other resources to identify unusual activities. You can set your firewall and other network tools to note any anomalous activities on your network.
- Collect clues about IoCs that exist within your environment. Use every available tool within your control to gather data relating to identified threats and unusual traffic on your network.
- Run analyses to study and learn from these IoCs. Mitigation is key when it comes to cyber threats and attacks. Strong foundational knowledge helps you achieve this goal by learning to identify potential and known threats.
Real World Examples of Cybersecurity Indicators of Compromise
So, what do cybersecurity IoCs look like in real-world settings? The FBI and Cybersecurity Infrastructure Security Agency (CISA) often release reports on cybersecurity threats and events worth highlighting. These reports typically include indicators of compromise that organizations and businesses can learn from and apply to enhance their cyber defenses.
A few recent examples of these reports include:
- #StopRansomware: Zeppelin Ransomware — We touched on this one at the beginning of this article. This Joint Cybersecurity Advisory report from the FBI and CISA details the IoCs and TTPs associated with the Zeppelin ransomware variant. The IoCs that they included were 162 MD5, SHA1 and SHA-256 hash values.
- RagnarLocker Ransomware Indicators of Compromise — This April 2022 report provided information relating to the RagnarLocker ransomware, which has targeted more than 52 organizations across 10 critical infrastructure sectors since January. The indicators of compromise recorded in this alert included dozens of:
- Bitcoin addresses
- Email addresses
- IP addresses
Resources You Can Use to Stay Abreast of and Implement Cybersecurity IoC Information
So, where do you look for useful information and mitigation strategies for IoCs? After all, it’s hard to put them to use as part of your cyber defense plan if you don’t know what you’re looking out for. There are many great resources online that can provide you with information on indicators of compromise. Here are a few in particular that provide excellent information:
- FBI and CISA Alerts — The FBI and CISA are great resources for information relating to malicious threats and attacks. Their reports share great insights and IoCs associated with various cyber threats, including ransomware. Click on these two links to view official CISA updates and FBI updates.
- MITRE’s CVE Program and Database — This database is a (which is moving over the next several months to the new CVE website (cve.org).
- NIST National Vulnerability Database — This website is the National Institute of Standards and Technology’s own version of a national vulnerability database.
IoCs can be used to create a holistic picture of threat activities and threat actors. But once you have all of this information, what can you do with it? You can use this information along with highly regarded industry frameworks and best practices.
MITRE ATT&CK® Framework
According to CISA, the MITRE ATT&CK® framework is a wealthy resource of information relating to cyber attackers’ tactics, techniques, subtechniques, and procedures based on real-world cyber events and observations. This framework can be used to “identify defensive gaps, assess security tool capabilities, organize detections, hunt for threats, engage in red team activities, or validate mitigation controls.”
When people talk about this framework, they’re typically referencing the ATT&CK framework for enterprises in particular. This resource is great for analyzing and responding to cyber security incidents and events. It also provides useful information for security validation, threat detection improvements, and assessments.
CISA released the Best Practices for MITRE ATT&CK Mapping, another great resource that breaks down best practices relating to mapping bad guys’ behaviors to known techniques.
Some Cybercriminals Are Smart, So Relying on Cybersecurity IoCs Won’t Always Work
While it’s all good and well to use IoCs to your advantage, it’s not something that will fix all of your cybersecurity woes. Unfortunately, cybercriminals can be pretty savvy (annoyingly so) and have been known to use tools that enable them to “dump” or conceal the indicators of compromise so as to prevent your defenders from using these markers against them. Basically, if they feel that you’re going to detect them or their movements within your system, they’re going to do everything within their power — delete files and overwrite data — to mask or hide their activities.
Therefore, you still need to take a proactive approach to cybersecurity to make yourself a tougher target and prevent attacks as much as possible. This means:
- Following cybersecurity best practices
- Educating your employees
- Using strong network defense monitoring, detection, and response tools (or hiring a third-party security provider to do that for you)
- Keeping your software and IT systems patched
Remember: A dearth of cybersecurity indicators of compromise doesn’t mean that your systems haven’t been compromised. It may just mean that you haven’t discovered the compromise yet.
TL;DR: What IoCs in Cybersecurity Are and How You Can Use Them to Your Advantage
Alright, we’ve reached the end and are happy you stuck it out with us the whole way through the article. Of course, if you’re a “TL;DR” fan and are just joining us here, we’ve got the skinny on what you need to know about IoCs in cybersecurity:
- Indicators of compromise are the clues bad guys leave behind regarding their identities and/or attack methods.
- Common examples of IoCs include hash values, IP addresses, network or host artifacts, etc.
- IoCs and indicators of attack (IoAs) are related but different: IoCs are about using marker data from past events to respond to ongoing compromises and prevent future compromises, whereas IoAs are about detecting these things in the moment to stop attackers in their tracks when an attack is happening.
- Cyber defenders can (and should) incorporate IoC data into their cyber defense plans and strategies.
But just remember that using IoCs may not always be an option, depending on how savvy your adversaries are. This is because some bad guys know how to cover their tracks well and are careful not to leave markers behind for you or your team to find.
Keep an eye out in the coming weeks for our next article in the series that will walk you through some of the ways you can use IoCs to improve your cyber defenses.
[ad_2]
Article link
