[ad_1]
If you’re like most businesses, it’s your main communication channel with customers. Here are some email server security best practices you can use right away to help create a secure email server for your organization
Imagine you’re preparing for a hurricane that’s coming your way (we Floridians are well acquainted with this procedure). You install straps to help make your roof more secure. You pull all your lawn equipment, furniture, and other outside items into your garage or shed. You board your windows and doors and buy lots of food and water in case you’re stranded without power. But if you choose to leave your home’s exterior doors open as the storm moves in, you can kiss your house and everything in it goodbye. Similarly, this is kind of what it’s like when companies don’t bother implementing a secure email server.
Radicati estimates the total number of business and consumer emails sent and received per day will surpass 376 billion by the end of 2025. If you send emails but don’t have a secure email server, then it means that any data transmitted through them is at risk of compromise. (Data is the lifeblood of your business — you can’t risk your sensitive info falling into the wrong hands.)
But what does it mean to have a secure email server? Let’s cover 10 email server security best practices and remind you why implementing these measures is necessary to protect your business and customers.
Let’s hash it out.
What Is a Secure Email Server?
Much like the word secure implies, having a secure email server means that you’re protecting your email domain and data from unauthorized usage. This means:
- Protecting your emails both when they are in transit and sitting in your employees’ inboxes
- Preventing unauthorized users from sending emails using your organization’s domain
- Setting up email filters and antivirus protection on your servers
- Securing the network(s) your employees and other authorized users use to access these email services
- Ensuring that your email servers are physically inaccessible to unauthorized parties (if you run your own email server)
- Understanding what steps your business email service provider (Amazon WorkMail, Google Workspace, Rackspace, Microsoft Exchange, etc.) takes to secure the server(s) that will host your organization’s email-related data
But how can you achieve these outcomes? Let’s dive right into what you came to learn…
10 Email Server Security Best Practices You Implement Now
The following email server security best practices list isn’t a complete or comprehensive guide. However, this list provides you with a great starting place to help make your email server more secure.
1. Change All Default Configurations, Usernames and Passwords for Your Email Server
A big mistake that organizations make is not taking the time to change their servers’ default settings and configurations. This may be because they’re in a rush or, perhaps, they don’t realize just how risky it is to use the default settings. Regardless of the reason, be sure to take the extra step and change these settings.
This includes changing default login information as well. Account and password security are paramount in cybersecurity as a whole. If you use a default username and weak password combo to secure anything, it’s the equivalent of having the option of using a double deadbolt lock on your front door but opting to use a flimsy chain lock instead. Sure, it provides minimal security, but an attacker only needs to use a little “brute force” (get it?) to bust their way in and gain access to your home.
Using the default credentials (username and password) that comes with your server or software is like this. It’s not secure and leaves your email server and its data at risk of theft and other compromises.
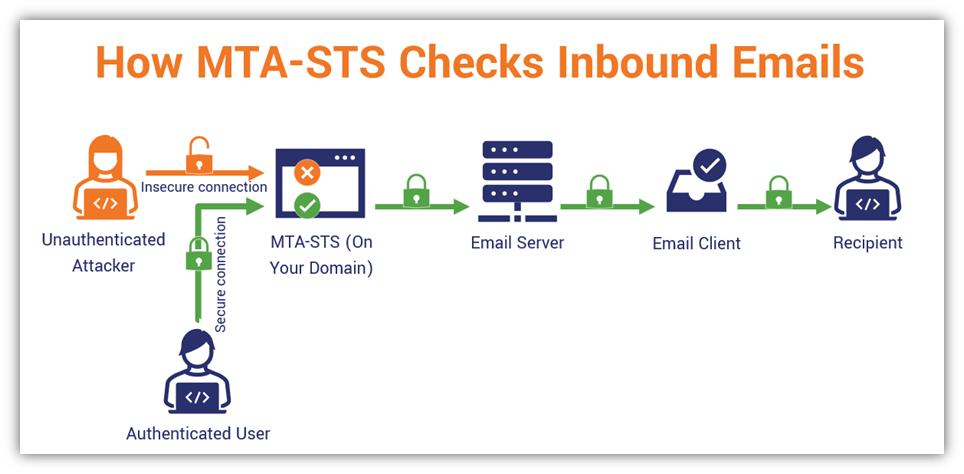
2. Set Up Mail Transfer Agent Strict Transport Security (MTA-STS)
A mail transfer agent strict transport security is a verification check of incoming emails. According to Google, “SMTP connections for email are more secure when the sending server supports MTA-STS and the receiving server has an MTA-STS policy in enforced mode.”
Uh, sure. Great. But what does this mean? Basically, this is saying in layman’s terms that if you have MTS-STS enabled on your organization’s email server, it’ll only permit emails to be received via secure, authenticated connections (using TLS 1.2 or 1.3).
This helps protect your recipients against receiving unauthenticated messages sent via insecure connections (i.e., connections where someone could insert malware or modify data in transit, or what’s known as a man-in-the-middle [MitM] attack).
If the sender’s digital identity can’t be authenticated or they didn’t have SSL/TLS enabled, then the message gets rejected.
3. Select Secure Email Protocols to Protect Your Communications in Transit
Setting up a secure MTA is only part of the equation; you also need to take a few extra steps to help make your server — and the inbound and outbound communications to/from it — more secure.
Install an SSL/TLS Certificate on Your Server to Enable HTTPS
Did you know that SSL/TLS also applies to email? That’s right, you can use SSL/TLS security to secure the communication channel of your messages. This allows you to encrypt the communications that transpire between your email server and other email servers that it communicates with. This way, no one can intercept the communications in transit.
Every time one of your employees sends or receives an email from someone, it creates a connection with that individual’s email server. If that connection isn’t secure, it means that anyone with the know-how can intercept that message in transit and steal or modify the data without the two original parties knowing what happened.
Of course, if you’re using an email signing certificate to encrypt your email data directly (more on that later), then this serves as an additional layer of security for your communications.
Use Secure Ports for Your Inbound and Outbound Email Services
Traditionally, IMAP or POP3 are protocols that are used for incoming emails (i.e., messages email clients grab from your mail server). SMTP, on the other hand, is used for outgoing emails. Be sure to set your services below to the following secure TCP/IP ports for incoming out outgoing messages:
- Outbound — Secure port 465 or 587 (with STARTTLS enabled) for SMTPS
- Inbound — With SSL/TLS enabled, you can use one of the following ports:
- Port 993 for IMAP (with SSL enabled)
- Port 995 for POP3 (with SSL enabled)
4. Embrace DMARC to Help Prevent Brand Domain Spoofing
Cybercriminals love playing dress up with companies’ brands and capitalizing on their reputations. It’s not uncommon for bad guys to impersonate organizations as a way to carry out phishing scams. Check Point reports that the most impersonated brand of Q1 2022 was LinkedIn, which was involved in more than half (52%) of all phishing attacks they analyzed globally. In Q4 2021, Check Point said that DHL held that title, and Microsoft prior to that was the reigning champion of the title that no company wants.
Domain-based message authentication, reporting and conformance (DMARC) is an email protocol that helps to protect your domain against inauthentic usage by unauthorized individuals. The Internet Engineering Task Force (IETF) brought it into the fold as a way to help organizations protect their domains against these fraudulent usages. DMARC builds upon two other authentication protocols to ensure that only your authorized users are sending emails on behalf of your domain:
- Sender policy framework (SPF): An SPF text is a record you attach to your domain name system (DNS). This helps to validate messages that are sent by your domain.
- DomainKeys identified mail (DKIM): This protocol attaches your digital signature to outbound email message headers. This allows you to use public key cryptography to help prove the authenticity and integrity of the emails that come from your domain.
But just how popular is DMARC? Mimecast reports in their report The State of Email Security 2022 that nearly nine in 10 companies (89%) are either using DMARC or plan to do so over the next 12 months. This is according to their global survey of 1,400 IT and cybersecurity professionals from 12 countries.
Of course, you can take DMARC a step further and bring your organization’s digital identity to the next level. You can do this by integrating brand indicators for message identification (BIMI) and verified mark certificates (VMCs) in your organization’s email digital identity. Doing this will enable you to insert your organization’s verified logo into all of your organization’s outbound emails from legitimate senders.
5. Keep Your Server Software and Firmware Current with Patches and Updates
Running an outdated or unpatched version of your server’s software is a surefire recipe for disaster. Patches are a publisher or developer’s way to fix bugs and other issues that leave your email servers vulnerable. If you don’t apply those patches in a timely manner, you run the risk of cybercriminals exploiting these vulnerabilities to gain access to your email server(s) and data.
Something you’ll need to choose is how you want to implement updates. Do you want to handle them manually? Do you want to explore the option of automation? Each approach has its pros and cons, but the point is that you need to ensure that updates and patches don’t fall between the cracks and don’t find yourself facing another Eternal Blue situation.
(Quick explanation: Eternal Blue was a vulnerability in legacy Windows systems that Microsoft issued a patch for but organizations neglected to roll out in a timely manner. The end result was hundreds of thousands of devices globally being infected by ransomware in an attack that impacted hundreds of millions of people [if not more].)
6. Use Email Server Firewalls to Keep an Eye on Inbound & Outbound Traffic
Alright, we’re more than half way through our list of secure email server best practices. Much like how network firewalls operate, email server firewalls filter inbound and outbound traffic based on the rules on your email server. What this does is help you to keep tabs on incoming and outgoing communications on your domain to look out for any suspicious activities.
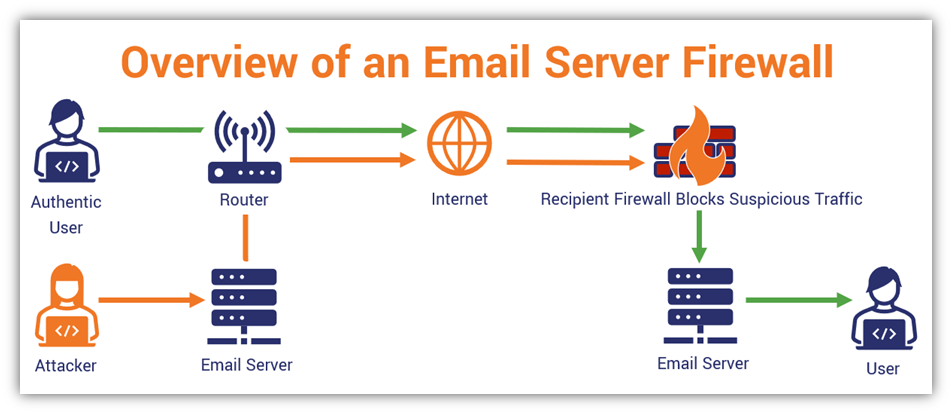
Of course, we can’t give you any specific directions about setting up rules on your email server since every system is different. So, you’ll need to refer to your specific firewall manufacturer’s site for specifics on how to accomplish this goal.
Set Rate Limits and Size Restrictions on Outbound Traffic
While it’s important to monitor your traffic, you’ll also want to be sure to restrict both the number of emails that can originate from your domain as well as their sizes. A spike in outbound messages could indicate that one or more of your authorized accounts could be compromised and is being used to send spam or phishing messages. Setting rate limits can help protect your domain’s reputation.
7. Be Selective in Who (or What) You Give Access to Your Mail Server
We’ve said it before and will continue to say that not everyone needs access to everything. This is true regarding everything from customer and employee database info to privileged access to your email servers. This is where access management best practices come into play.
You can set employee profiles so that users have only the minimal level of access they need to do their jobs. If someone needs access to a sensitive system for a project, assign them permission for the amount of time necessary to complete it. Be sure to remove those privileges once that access is no longer necessary (e.g., when they complete the project).
Furthermore, be sure to have a procedure in place that ensures access is revoked for accounts when employees leave your organization. Attackers or even disgruntled former employees love to use old logins to nose around systems they should no longer have access to. You can prevent this from occurring by deactivating their accounts right away.
8. Use Secure Passwordless SSH Authentication as Admin to Manage Your Server
As an administrator, you likely use secure shell (SSH) to manage your organization’s various servers. Traditionally, this requires using a username and password combination for authentication. But there’s a better (and more secure) way of doing that than relying on potentially weak login credentials: you can use public-private key pairs instead.
This method of authentication involves using cryptographic keys to prove your digital identity as a legitimate authorized user. One of which is public and the other your device keeps private that proves you’re you. This process enables you to authenticate easily and securely without ever having to remember a cumbersome password.
We’ve talked at length about the importance of SSH key management best practices previously. To quickly recap, SSH key management is about securing your cryptographic keys as part of your SSH access management strategy and security practices. (Be sure to check out the article linked at the beginning of this paragraph for more in-depth information.)
9. Teaching Users How to Keep Their Accounts Secure
Protecting account credentials isn’t optional; it’s the responsibility of every individual employee and network user. Why? Because compromising users’ accounts is the easiest way for hackers to compromise your server. Part of this approach to hardening your organization’s cyber defenses involves educating and training users on cyber security best practices.
Some of the things effective cyber awareness trainings should cover include:
- How to recognize and avoid social engineering and common phishing threats (use real-world examples for this)
- What they should do when they receive suspicious emails or phone calls (provide specific guidance and contacts)
- How to create secure passwords (which you’ll need to enforce)
- How to use single sign on (SSO) and password management tools
- Why they shouldn’t install shadow IT (unauthorized and potentially malicious software)
10. Require Your Authorized Users to Digitally Sign and/or Encrypt Their Emails
To help prevent your employees — especially admins and other privileged user — from falling for credential phishing scams, require everyone to digitally sign their emails. By adding a cryptographic digital signature (i.e., a signature that’s verified by a public CA) to your email, you’re doing two big things:
- Offering an email recipient assurance that the sender is legitimate, and
- Ensuring the message’s integrity hasn’t been compromised since it was signed.
You can also use these certificates to encrypt emails containing sensitive data for added measure. This process requires both parties (sender and recipient) to have email signing certificates, and for the email sender to use the recipient’s public key. You then use their public key to encrypt the email before pressing Send and they use their corresponding private key to decrypt the message on their end.
If this sounds complicated, don’t worry — all you have to do is ask the recipient to send you a digitally signed email first. This way, you have a copy of their public key readily available. It’s that simple.
Final Thoughts on Why Having a Secure Email Server Is a Must for All Organizations
Frankly, there are many reasons why implementing these email server security best practices is crucial for businesses and other organizations globally. The biggest reason is that it’s the right and responsible thing to do. Your customers, users and other stakeholders are entrusting you to protect their data.
Second, it helps to protect your interest by keeping your data secure from prying eyes. Cybercriminals or even your competitors would love to get their hands on the digital goodies you have stored on your email server.
Here are a few other quick reasons why having a secure email server is essential for your organization:
- Keeps your data secure from unauthorized access
- Prevents data breaches and compromise
- Avoids the brand and reputational damages that will result from security issues
- Ensures compliance with data privacy and security regulations (GDPR, CCPA, PCI DSS, etc.)
- Mitigates the risk of having to face direct and indirect costs of having an insecure email server (think data breach mitigation, lawsuits, noncompliance penalties, etc.)
[ad_2]
Article link
