[ad_1]
PKI is everywhere — it secures everything from websites and emails to the smart devices you use to secure your home and business. It’s the hero operating in the background that you don’t know exists unless you know where to look…
What do your smart coffee maker, our website, and a nuclear power plant have in common? They all rely on public key infrastructure (PKI) behind the scenes.
But why is PKI so popular? It’s the secure, tried-and-true way to:
- Identify and authenticate authorized users and devices
- Encrypt data transmitted between two parties or systems
- Protect software, documents, and other data from unauthorized modifications
- Add another layer of security to your public and private IT environments and assets
But what are some examples of specific PKI uses and applications your organization can adopt? It’s time to explore PKI use cases.
Let’s hash it out.
Breaking Down Potential PKI Use Cases Within Your Organization
Public key infrastructure is the framework, underlying technologies, policies, and protocols that make secure communications possible over the internet. Before PKI arrived on the scene in the mid- to late-1970s, you’d have to meet in person to exchange encrypted messages.
But rendezvousing whenever you need to exchange a secret message really hampers international communications and business opportunities. Not to mention the impact that would have on your productivity, operational efficiency, and your bottom line… (yikes).
PKI can be used to secure public and private resources:
- Public PKI uses — This uses digital certificates from publicly trusted certification authorities (CAs) to secure connections on public-facing assets (websites, web apps, public-facing services, etc.)
- Private PKI uses — You can create a private certification authority (CA) that 1) authenticates your organization’s devices and users, and 2) secures access to your internal apps and web apps, intranet sites, endpoint devices, and other internal resources.
Let’s explore several ways to use PKI within your organization to secure your public and private assets.
PKI Applications: Securing Your Public Website, Web Apps and Services
When people think of PKI use cases, they typically think of website security certificates (i.e., SSL/TLS certificates). These digital certificates encrypt website connections and verify the digital identities of the organizations that control the sites. The web server provides its certificate to the connecting client during the SSL/TLS handshake at the beginning of the session.
1. Secure, Encrypted Connections for Websites
Installing a valid SSL/TLS certificate on your website lets you add transport layer security (previously secure sockets layer) to your otherwise insecure hypertext transfer protocol (HTTP) connection. Without it, bad guys could intercept your plaintext data in transit.
Think of all those tempting usernames, passwords, and other sensitive data that users are transmitting to your web server, which could land in bad guys’ hands if you don’t enable HTTPS…
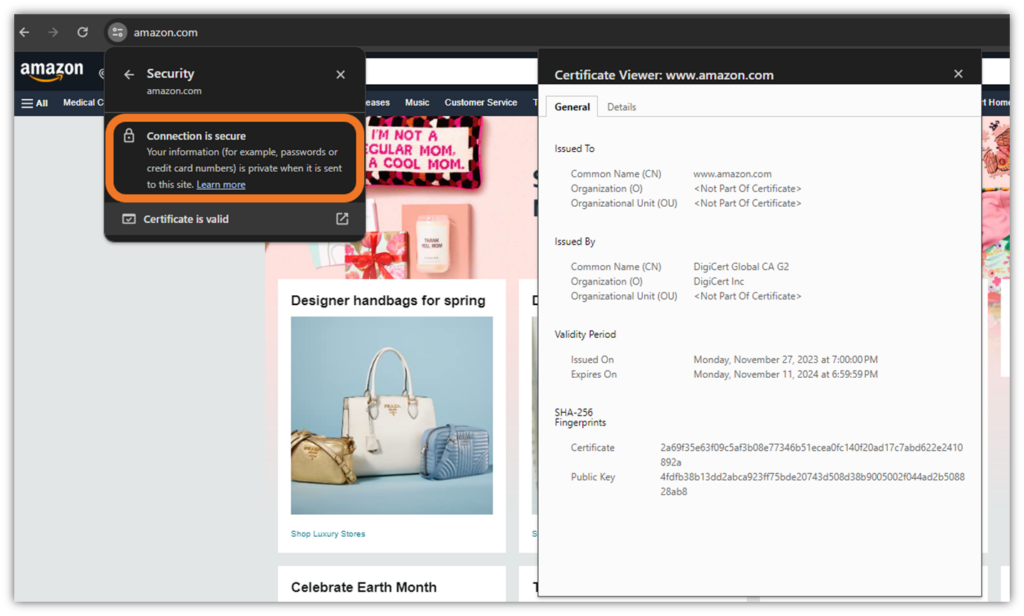
2. Digital Identity Validation (Authentication) for Websites
Depending on the validation type of SSL/TLS certificate, a certificate can provide verified organizational details about your organization. This way, users’ web clients know your site is legitimate and that your organization truly runs it.
This is what an SSL/TLS certificate looks like in Google Chrome:
PKI Applications: Authenticating Users & Devices Without Passwords
Data from IBM’s 2024 X-Force Threat Intelligence Index 2024 report indicates a significant shift in how bad guys are infiltrating organizations’ networks and systems. Rather than sneaking through a back window (hacking), they’re walking in through the front door instead (i.e., logging in using compromised credentials).
It’s no secret that passwords are vulnerable to phishing and social engineering tactics. They can also be leaked or stolen due to poor secrets management practices and security misconfigurations. Want some good news? You can bypass using passwords and opt for public key infrastructure-based authentication instead.
So, what PKI uses can mitigate many of these risks and reduce your attack surfaces? These are all excellent options for an internal PKI to handle.
3. User Authentication
User authentication (also called client authentication) spans the gamut, encompassing everything from certificate-based identity for Active Directory user profiles and physical ID badges you issue to employees to the S/MIME certificates you use for digitally signing and encrypting emails. Basically, the key ingredients for identity and access management.
You can have multiple user certificates installed on a single machine, but each user is restricted to authenticate to the systems they’re authorized to access. This helps you verify that only authorized, authenticated users can access internal apps, intranet sites, and other resources.
4. Wireless Network Authentication
PKI-based Wi-Fi access allows authorized users to prove their digital identities without entering passwords that would otherwise be susceptible to man-in-the-middle (MitM) and evil twin attacks. This way, they can access your Wi-Fi network(s) while keeping their certificates’ private keys securely stored on their devices’ trusted platform modules (TPMs).
5. VPN Authentication
Likewise, PKI-based VPN authentication allows authorized users to connect to your virtual private network without exposing their credentials while trying to forge secure, encrypted connections.
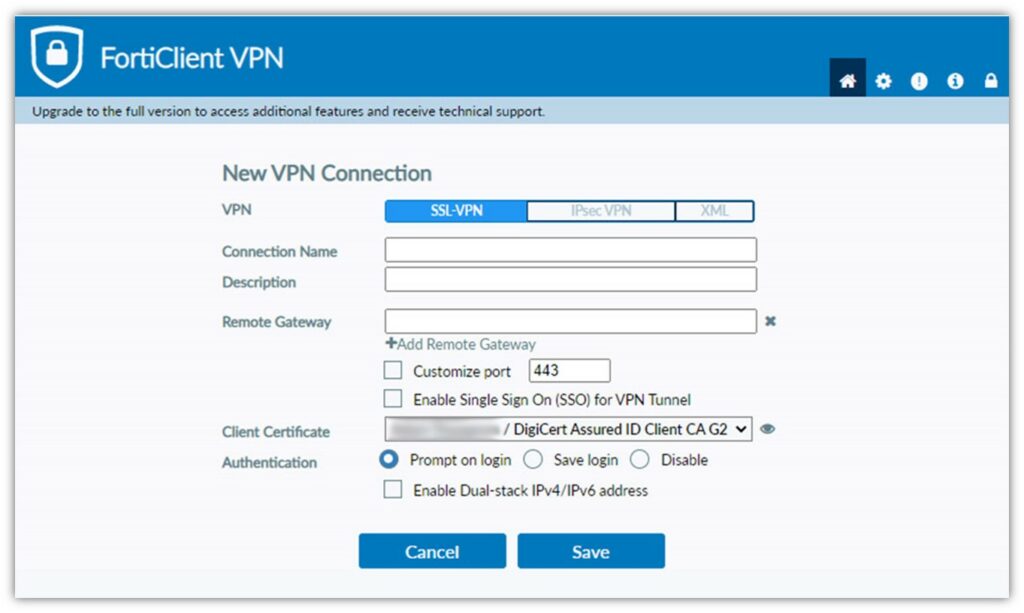
6. Device Authentication
PKI certificate-based device authentication helps you secure your devices and the system(s) they connect to. It allows you to verify that a device is legitimate and can access authorized systems easily. A device certificate validates the device itself and not a specific user who may access it. It’s ideal for authenticating and securing the following:
PKI Applications: Securing and Authenticating Emails
It’s no surprise that email is the go-to communication method for most businesses nowadays. It’s virtually instantaneous, convenient, and way less expensive than mailing physical pieces (which could get lost or damaged in transit).
But with all of the benefits that emails provide, there are also drawbacks — namely, they can be spoofed and are at risk of being intercepted or altered in transit. But this is where PKI can save the day. There are several important PKI-related use cases and applications:
7. Email Digital Signatures
An email digital signature is a nifty tool that assures email recipients that the message is authentic (i.e., the sender is who they say they are) and that the message hasn’t been altered in transit. Creating an email digital signature requires only the signer to have an email signing certificate (or what’s often called an S/MIME certificate).
Depending on whether you use a publicly- or privately trusted certificate, the legitimacy of your digitally signed emails can be verified by internal and/or external users.
8. Secure, End-to-End Email Encryption
This is a security mechanism for sending secure, encrypted messages between two parties who both use S/MIME digital certificates. Using the recipient’s public key, the sender can encrypt the contents of the email before it leaves their mailbox. This provides end-to-end security, ensuring the message is secure when it sits in the recipient’s inbox.
Email signing certificates apply to examples #7 and #8 because they make digital signatures and email encryption possible. Furthermore, these certificates can apply to public and private PKI uses and applications. NOTE: Some new multipurpose S/MIME certificates also provide additional functionalities, such as limited document signing and client authentication capabilities. (We’ll speak more about document signing momentarily.)
Here’s an example of what a digitally signed and encrypted email looks like when you have the necessary decryption key:

9. Email Server Authentication
SSL/TLS can be used to secure and authenticate connections between mail servers, too. (NOTE: This doesn’t encrypt the message itself, only the connection.) For example, SMTP connections are not encrypted by default, meaning that they’re vulnerable to interception by bad guys.
This is why we, like Microsoft, recommend always securing email transmissions using public key encryption.
However, Google has gone beyond just offering it as a recommendation. A December 2023 Gmail update makes it a requirement to install an SSL/TLS certificate on your email server. Doing this enables server authentication and ensures messages are sent via secure connections.
10. Displaying Verified Company Logos in Email Inboxes
A verified mark certificate (VMC) is a newer digital certificate that ensures brand name recognition from the get-go. Using this type of publicly trusted certificate, in combination with brand indicators for message identification (BIMI) and domain-based message authentication, reporting and conformance (DMARC), allows you to display your trademarked logo next to your email in users’ inboxes.
With a VMC and BIMI, you no longer have to rely on users unquestioningly trusting your emails enough to click on them. Instead, you can assure recipients the emails are authentic by displaying your trademarked company logo up front:
Want to get a VMC? Let our Sales team know, and we’ll gladly help you get started.
PKI Applications: Proving Your Documents’ Are Legitimate and Unaltered
Your organization’s contracts and documentation are important. No one, especially not your c-suite execs, wants someone tampering with those files after the fact. This is why it’s crucial to sign your Microsoft Office documents and Adobe PDF files using a document signing certificate.
11. Sensitive Office File and PDF Protection
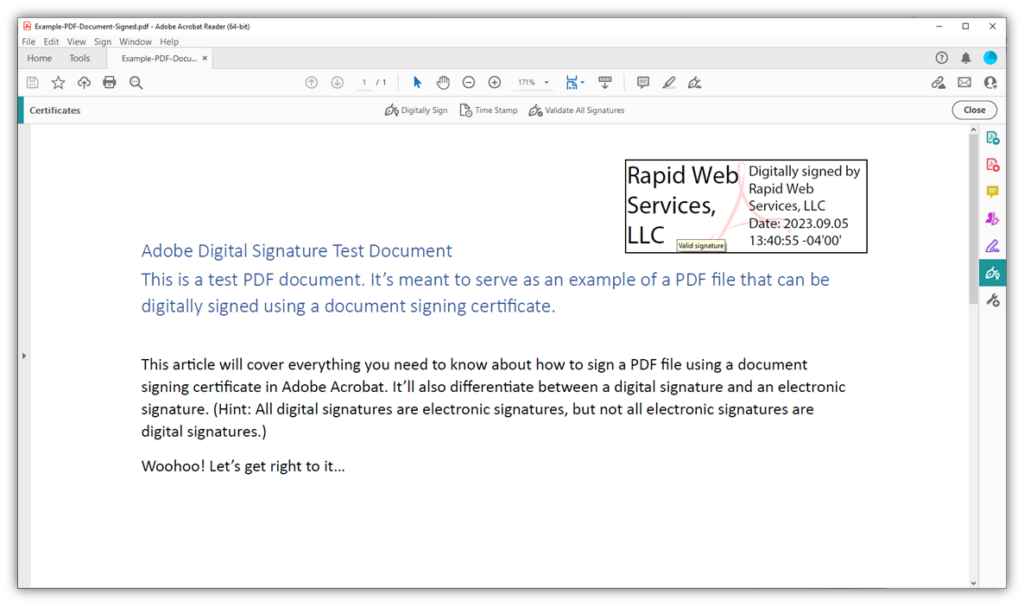
If you already have one of the multipurpose S/MIME certificates we mentioned earlier, then you’re in luck because it already gives you the ability to sign Microsoft Office files. But if you don’t have one, or are interested in also signing PDF files, then check out our document signing certificates.
Here are a couple of ways that document signing can be beneficial:
- Assert your verified digital identity using a cryptographic digital signature
- Verify whether the document has been altered since it was signed
- Build digital trust, which benefits your company’s brand and reputation
Of course, there’s a huge risk if the signing keys were to fall into the wrong hands. This is why document signing certificates must be stored on secure hardware, such as in secure USB tokens, hardware security modules (HSMs), or using cloud-based signing solutions that use HSMs.
Related resource: How to Digitally Sign a PDF in Adobe Acrobat (A Step-By-Step Guide with Pics & Video)
12. EU Qualified Electronic Signatures (QESes)
PKI makes it possible to deliver eIDAS-complaint qualified electronic signatures for important personal and professional applications. The 2014 eIDAS Regulation (910/2014) set the groundwork for using PKI-based digital signatures that can be created and validated anywhere in the European Union.
An eIDAS-qualified electronic signature uses PKI to create a verified digital identity and protect the file’s integrity using hashing. It relies on:
- A qualified certificate for electronic signatures to give you a cryptographic digital signature that’s recognized as the equivalent of your handwritten signature.
- The private key that’s used to sign is generated using a qualified signature creation device (QSCD).
The new eIDAS 2.0, which was approved on Feb. 29, 2024, will kick into effect this year. (The official effective date will be 20 days after the updated regulation is published in the EU’s Official Journal.) This regulation, which will amend the 2014 standardized framework for electronic digital trust and identity services in the EU, gives citizens and residents the ability the option of using a European Digital Identity Wallet.
PKI Applications: Protecting Software Integrity & Software Supply Chains
13. Software Identity and Integrity Protection
Want to keep your apps and code as secure as possible? Then sign your software products using a publicly trusted code signing certificate. This process uses a private key and cryptographic functions to create a digital signature that builds trust with Windows operating systems over time.
This approach ensures your software displays your verified digital identity and creates a checksum that informs users’ devices when your software has been altered. By signing your software, you’re helping protect your customers’ software supply chains by giving them a way to verify your apps and updates are authentic and haven’t been tampered with since they were signed.
Of course, as with a document signing certificate, a code signing certificate’s private key must be stored on secure hardware. This is an industry baseline requirement (certificates are issued with a secure USB token by default). This way, authorized users can use the keys without having direct access to those secrets.
Here’s are two quick examples of what users may see when attempting to install your unsigned or signed software program:
Example #1: Microsoft Defender SmartScreen
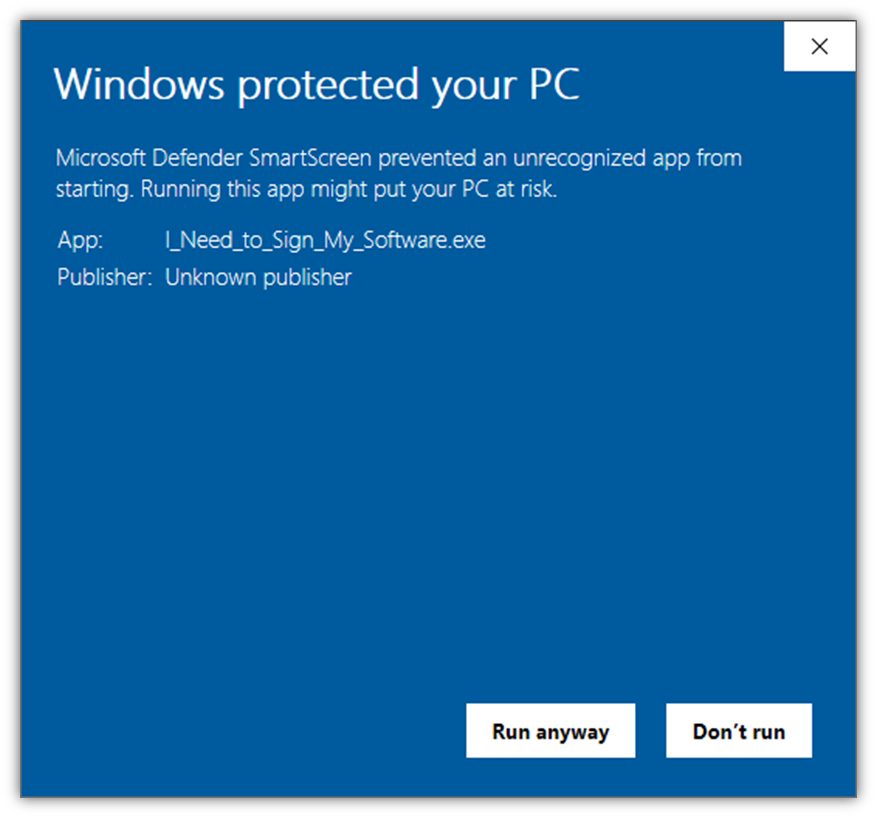
Image caption: A screenshot displaying what unsigned software looks like in Windows Defender SmartScreen.
Example #2: Windows User Account Control (UAC)
If the Microsoft Defender SmartScreen warning message doesn’t display, users will likely see a UAC window instead:
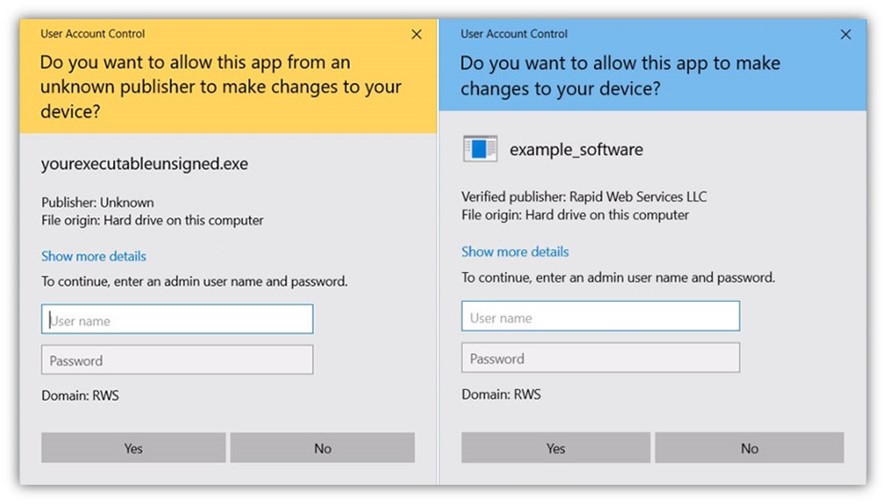
Which message do you think is going to have the more positive outcome in terms of users going through with installation? Certainly not the left message.
14. Software Component Authentication
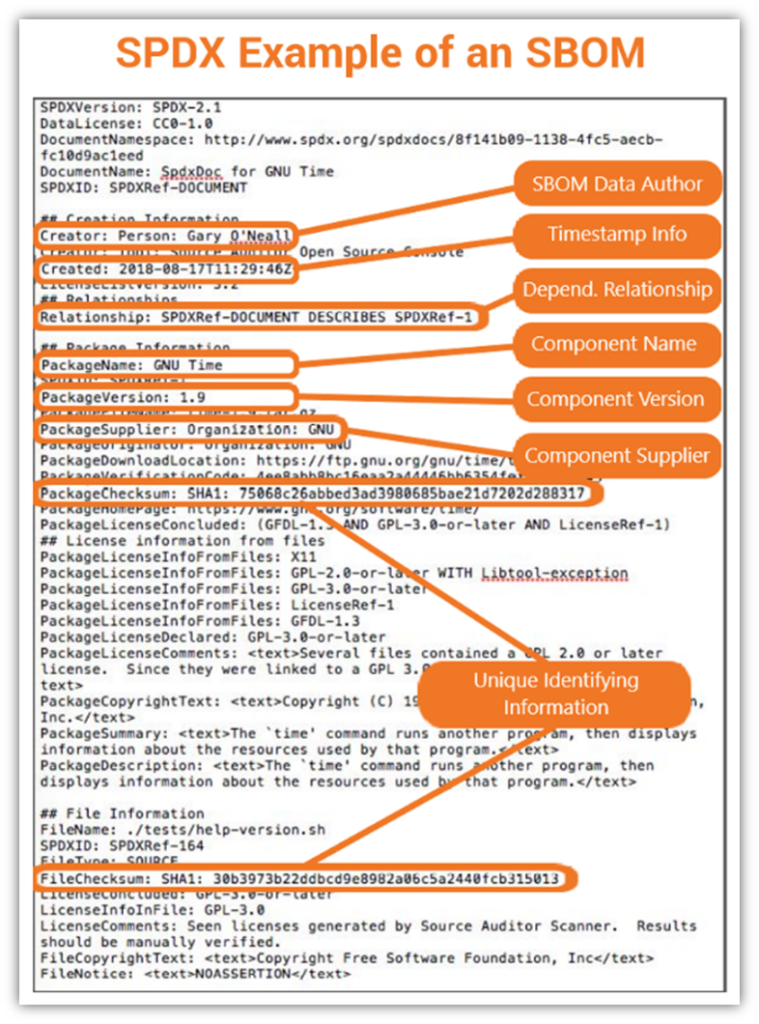
A software bill of materials (SBOM) is a list of the components that went into creating your software. This includes all third-party dependencies and open-source code. You can sign your SBOMs using a cloud-based code signing service.
Signing your SBOM adds another layer of security to your software app and helps customers feel more confident using your product by:
- Providing an authenticated list of its components (so users know it’s legit)
- Proving the origins of its code (digital provenance).
15. Authenticate Your Over-the-Air Updates
It’s no secret that many IoT manufacturers don’t update or patch their products after release, leaving them vulnerable to exploitation by bad guys. But what if you’re an IoT manufacturer who publishes regular updates? If you want to ensure that all of your firmware patches and other software update releases are trusted and arrive unaltered, then a good way to proceed is to sign your OTA packages.
These updates enable you to deploy OTA updates remotely via the cloud, requiring no physical intervention from users who can install updates quickly and easily. Think of the updates that Apple device users receive on their iPhones and iPads, or the updates Tesla owners receive to their electric vehicles.
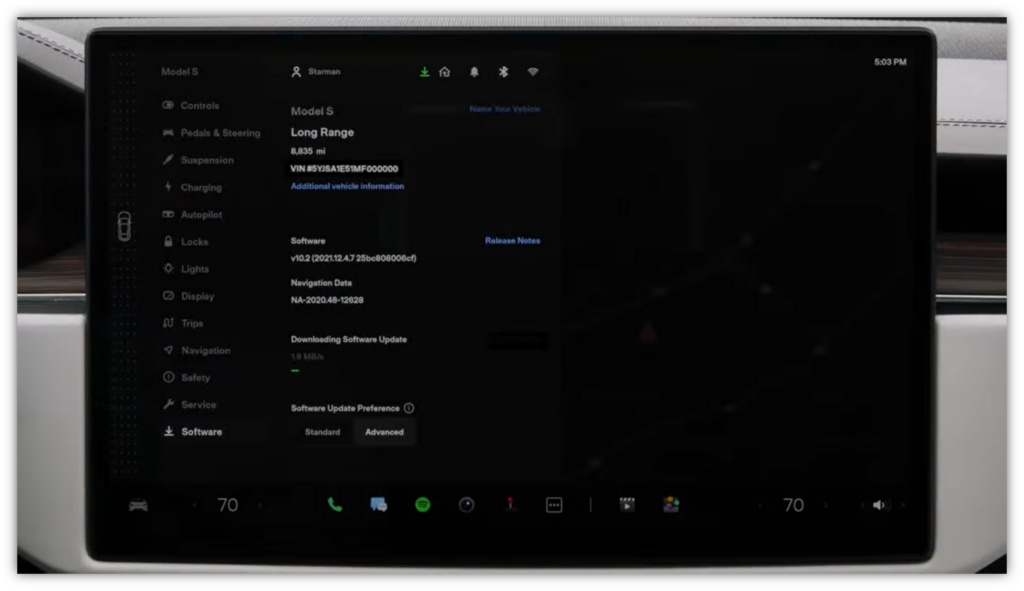
Image caption: A screenshot from Tesla’s Model X software and support video, which shows the company’s OTA software updates screen.
PKI Uses: PKI Only Works If You Properly Manage
None of these public or private PKI implementations will do any good if you don’t bother to properly manage the certificates and keys that make them possible. Whether it’s keeping your mobile or IoT device certificates up to date, storing your keys securely, or managing access for network users, your ability to have the proper PKI management processes and policies in place can make or break your organization’s security.
One important way to overcome PKI management-related challenges is to use automation. PKI automation simplifies the certificate and key lifecycle management process. It frees up your IT-related work hours and simultaneously helps harden your organization against future threats.
Wrapping Up on PKI Use Case Examples
Public and private PKI touch virtually everything in modern businesses. This includes everything from the security tools used to keep your websites, networks, and data safe to the identity and access management resources that control access to your most sensitive IT systems.
We’ve identified many of the ways your organization may capitalize on the benefits of PKI that you may (or may not) have previously considered. We hope you’ve found this introductory article useful and can help you feel more informed when approaching conversations about these uses and applications with your colleagues.
Are there additional use cases you’re interested in exploring? Reach out to our Sales team to learn what custom solutions we can create to meet your specific needs.
[ad_2]
Article link
