[ad_1]
From how specific cryptographic algorithms work to how countries are working to face down looming quantum threats, the November 2023 conference covered many topics. We’ve got 9 key insights and takeaways to share…
In early November, public and private cybersecurity and cryptography experts worldwide gathered in Amsterdam to share their insights and updates about quantum-resistant (quantum-safe) cryptography at the PKI Consortium’s latest conference. Some presentations focused on the technical details of PQC cryptographic algorithms and schemes, while others talked about the considerations surrounding the implementation of quantum-safe cryptography in specific environments.
The PKI Consortium is a non-profit organization comprising 100+ public and private member organizations (governments, certificate authorities, auditors, service providers, consultants, etc.) from around the world. This event marked the PKI Consortium’s second PQC conference, the first of which was hosted in Ottawa in Ontario, Canada.
Since we figured most of our readers didn’t get to make the trip to the Netherlands or want to get up as early as 3 a.m. to tune in remotely, we’ve put together a breakdown of some of the key takeaways and lessons we learned from this year’s sessions.
Let’s hash it out.
An Overview of the Top Concerns Haunting Organizations Regarding PQC Implementation
Before we dive into all of the top takeaways from this year’s conference, let’s quickly go over some of the key challenges that industry experts say organizations face when preparing for post-quantum cryptography.
Of course, this is only a handful of the challenges that public and private sector organizations may experience in the journey to a post-quantum world. Now, it’s time to explore some of the takeaways global industry leaders shared during the 2023 PQC conference.
Top 9 Takeaways For Public and Private Sector Stakeholders
1. We Need to Stop Calling It “Post-Quantum” Cryptography
Using a term like “post-quantum cryptography” doesn’t drive home the urgency of transitioning from quantum-insecure to quantum-resistant cryptography. The actual verbiage is still contested within the industry, though, as some experts refer to it as PQC while others call it “quantum-resistant” or “quantum-safe” cryptography.
Chris Hickman, Chief Security Officer at KeyFactor who presented and participated in one of the conference’s panel discussions, described the term “post-quantum” cryptography as the biggest disservice industry professionals did to themselves.
“This is an evolution of security, and we really need to start thinking of it in those terms,” said Hickman, who said that organizations need to start thinking through the security needs regarding these vastly different technologies now and not when quantum computers are widely available. He pointed out that the industry has been relying on the same technologies for several decades and that enough is enough. “What else has lasted for 40 years in IT, period? Not a lot. Security-wise, not a lot.”
“So, I think, yeah, things are going to take on their own life cycle and their own trajectory because organizations are going to start to realize that this is simply an evolution. This is the next step.
No, we’ve never been through this; yes, it’s going to be painful. Are we going to stumble along the way? Organizations will stumble along the way, that’s without question. But the thing that we can do here is help explain the best ways to do that, the ways to mitigate the risk, how to look at it from risk management standpoint. I think that’s a very smart way to look at it.”
— Chris Hickman, Chief Security Officer at KeyFactor
Hickman’s sentiments are shared by other industry experts, including Tim Hollebeek, DigiCert’s Industry Technical Strategist. He recommends referring to it as “quantum-safe cryptography” instead.
“The problem with the term post-quantum cryptography is that it is easy to misunderstand as something you don’t need to do until cryptographically relevant quantum computers (CRQCs) arrive, which that’s the exact opposite of true.”
— Tim Hollebeek, Industry Technical Strategist at DigiCert
2. Quantum Computing Is Something to Start Planning & Preparing For Now Using Hybrid Cryptography
A theme that was repeated throughout the two-day conference is that you can (and should) start planning and preparing for PQC rather than waiting. If you wait, you’ll already be too late. While saying companies should start planning and preparing is all well and good, but it leaves us with two important questions:
- How do we start preparing?
- And how soon do we need to do so?
One of the things highlighted by many speakers was having a hybrid quantum security strategy. The benefit of using PQC hybrid algorithms in your approach is that they still support the “classical” algorithms that are necessary to fight modern threats while also using PQC algorithms to protect data against “harvest now, decrypt later” attacks.
This means bad guys would have to break two cryptosystems in order to compromise data. This protects you while in the transition period when we’re not sure about whether the new PQC algorithms will work as intended. (After all, we’ve seen a number of NIST candidate algorithms being broken over the past several years using modern computers.)
We’ll talk more about the answer to the first question in just a moment. But as far as the answer to question #2 is concerned: start planning now. Quantum computers are becoming more advanced, and companies are working on “noise reduction” to help facilitate more powerful machines that require fewer qubits to operate. So, what does this mean for organizations with regard to when they need to start getting their ducks in a row?
“The main thing is, don’t wait. Well, we do want you to wait for the final standards. So, you can test out the algorithms now. You can get ready. Wait for the final standards to begin actually putting these into products. But for planning purposes, don’t wait to think about your migration – start getting ready for that.”
– Dustin Moody, Mathematician & Project Lead, Post-Quantum Cryptography at the National Institute of Standard and Technology (NIST)
3. A Cryptographic Inventory and Risk Analysis Are the First Steps to PQC Readiness & Agility
By and large, organizations are clueless about where and how they’re using cryptography within their networks and IT infrastructure. In some cases, the uses are internal; other times, they’re provided through third-party services and software.
But the key thing to remember is that if you don’t know what cryptographic assets you have or where they are, then you can’t identify your risks, and if you can’t do that, then you don’t know what you need to mitigate them.
- Creating an inventory of cryptographic assets and vulnerabilities. This involves using automated scanning tools and manual scanning methods to catch what they miss.
- Perform quantum risk analysis on top of your standard risk analysis. This will provide you with greater insights into the PQ vulnerabilities within your network and IT environment.
The next step is to prioritize where you want to start taking action and make preparations for “Q Day.” But how do you do that if you don’t know where your organization currently stands? This question is one Tom Patterson, Quantum Security Global Lead at Accenture, says he wants to help organizations globally figure out via a Quantum Security Maturity Index.
Patterson said the concept is similar to the Capability Maturity Model Integration (CMMI) in that it gives company boards and executives a way to measure where they are and see how far they still have left to go. If they’re at level 2 and want to be at level 3, what money and time would they need to invest?
His company is working with organizations across the world in multiple sectors to create standardized definitions relating to PQC adoption and maturity. The PQC journey the company has outlined currently has eight PQC maturity tiers that are part of Accenture’s program:
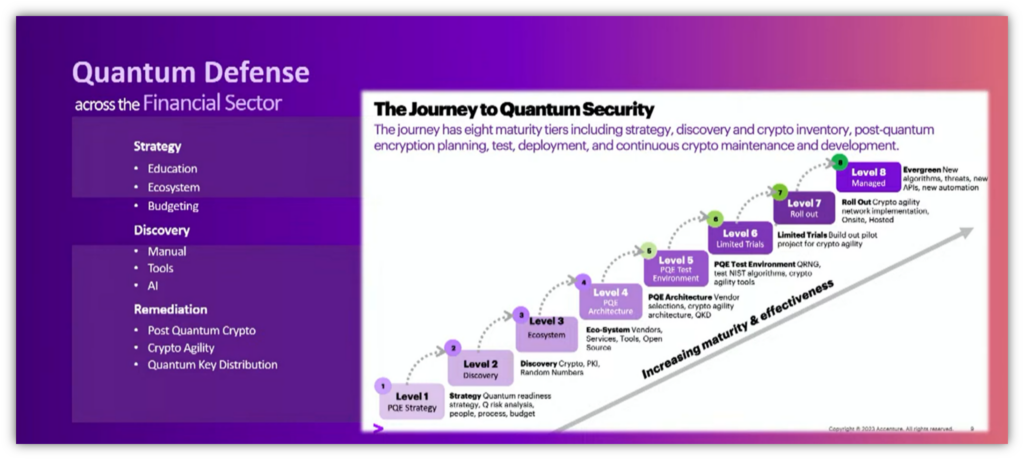
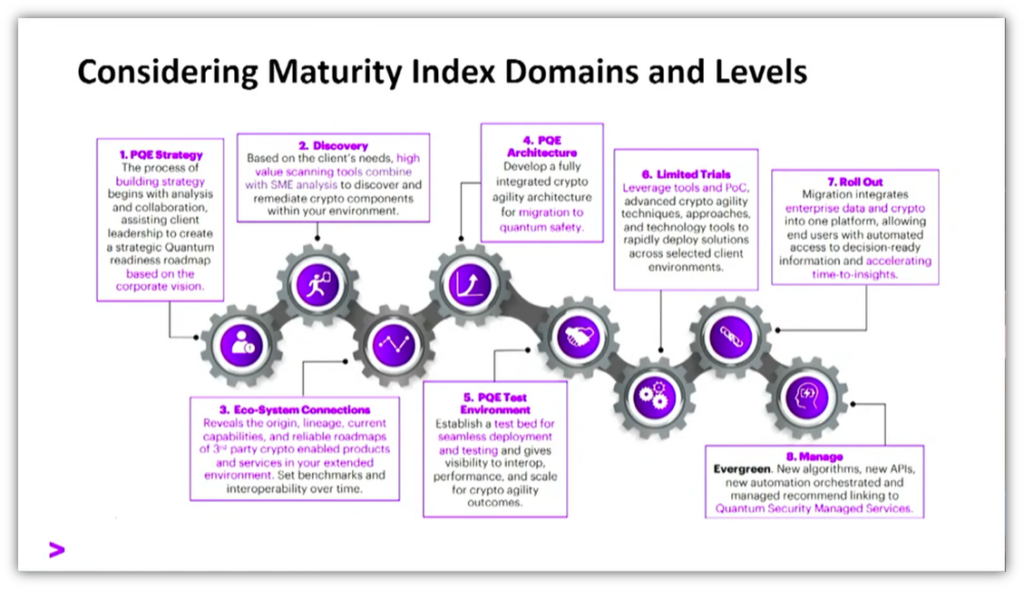
“I’m just trying to drive the process so that there’s standardized definitions about adoption and maturity,” said Patterson. “If you can’t measure it, you can’t protect it.’”
Where Does PKI Come Into Play in All of This?
That’s a good question — one Patterson hopes organizations will help him answer. After all, having a robust and PQC-safe PKI requires more than just swapping out a few existing assets.
“Because PKI is so robust in its current state, you can’t just tinker with it,” says Tom Patterson. Instead:
“We talk about how it is highly sophisticated and highly integral to their operations today, and just changing over from one HSM to another, and from one piece to another, from one certificate to another certificate. That’s not the answer. That’s not how it’s going to work.“
Changing the underlying foundation of internet security — all of the technologies, protocols, policies, and other components that make up public key infrastructure (PKI) — is a process Patterson says will take place over “many years going forward.” But if an agreed-upon maturity index is created through collaboration across organizations in various sectors, it’ll improve the overall quantum defenses of the world as a whole.
He put out a call for “volunteers” of sorts; organizations that want to participate in the process and help identify areas and specific steps to build out. Accenture is planning to unveil the results of this collaborative effort to the world at the World Economic Forum in January 2024.
4. NIST’s First PQC Standards Are Coming in Early 2024
Since 2016, the National Institute of Standards and Technology (NIST) has been engaged with the cryptographic community in a “competition” to create quantum-resistant cryptographic algorithms. (This isn’t a new approach, as RSA and other algorithms have been created in similar scenarios.) Although NIST has released drafts of the first three PQC algorithms for public comments, the federal standards organization is looking to publish the first official PQC standards early next year (2024).
Two experts from NIST — Dustin Moody, Mathematician & Project Lead, Post-Quantum Cryptography and Bill Newhouse, Cybersecurity Engineer & Project Lead, National Cybersecurity Center of Excellence (NCCoE) — shared the ongoing process regarding the selection of PQC algorithms. Their update offered insights into the NIST PQC standardization process, how it’s coming along, and practices to make migrating from quantum-vulnerable public-key cryptography to quantum-resistant cryptography a bit easier.
Here’s a quick timeline of the NIST PQC process:
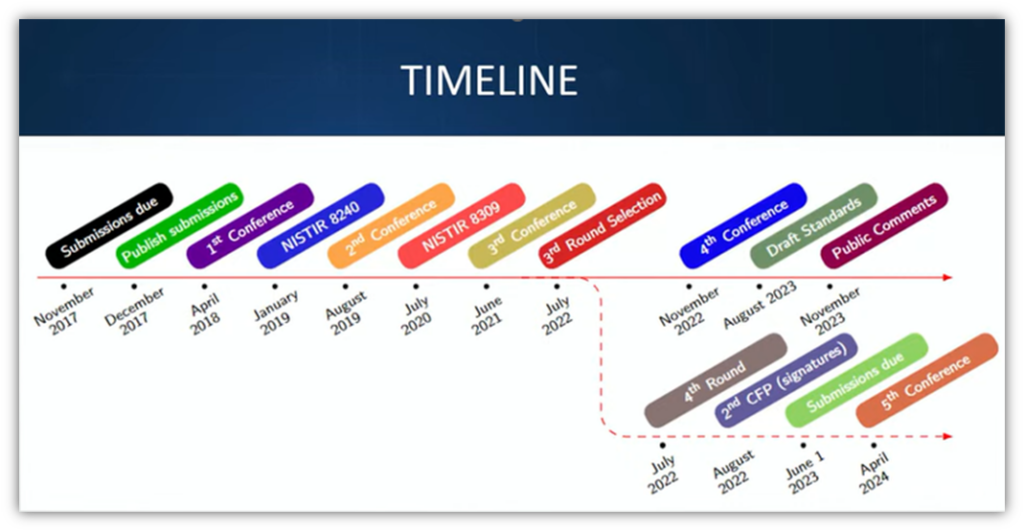
As of the writing of this article:
- NIST has completed four evaluation rounds for cryptographic algorithms.
- NIST opened a request for public comments in August (which are open until Nov. 22, 2023) on the first three drafts of the Federal Information Processing Standards (FIPS) for Post-Quantum Cryptography:
- Additional signature schemes are still being considered.
This “small call” for additional signatures, ideally based on code-based algorithms rather than lattice problems, aims to create greater diversity amongst the pool of PQC algorithms. The idea here is to have additional general-purpose signature schemes and those that have faster verification and shorter signatures for different use cases.
5. Being Crypto-Agile Is Crucial and Is Everyone’s Responsibility
Crypto-agility is described by Germany’s Federal Office for Information Security (BSI) as a principle of keeping cryptographic mechanisms ‘as flexible as possible in order to react to developments, implement upcoming recommendations and standards, and possibly replace algorithms in the future that no longer guarantee the desired level of security.’” This also entails being able to use existing secure hardware and systems to meet the needs of new cryptographic algorithms and protocols without hindering performance.
But what do the experts say about crypto-agility in terms of what it represents and how it should be perceived?
“Crypto-agility begins with agile standards,” said Jaime Gomez Garcia, Head of Quantum and Architecture at the Crypto and Blockchain CoE, Banco Santander, who emphasized that it’s constantly adapting and changing through collaboration. “Our new cryptography standard isn’t built as a Word document; it is built on GitHub.”
Bill Newhouse from NIST describes crypto-agility as a dream for public and private sector organizations alike. “It’s a desire, and some of you have mapped out schemes to support this within your technologies to support this.”
The overarching idea that many presenters reiterated is that everyone needs to keep cryptographic agility in mind when evaluating solutions. But Robert Hann, Global Vice President of Sales, Cryptographic Center of Excellence at Entrust, says that being crypto-agile is more than having the right tools in place:
“Crypto-agility is not just about tech; it involves people and processes. It’s a process of change, and many organizations aren’t good at changing cryptography because we’ve never had to try. We haven’t really been tested hard. We now are about to, so you’ve absolutely got to build that in, in the solutions you buy, the software you develop.”
— Robert Hann, Global Vice President of Sales, Cryptographic Center of Excellence at Entrust
6. By and Large, CISOs Won’t Adopt PQC Until They Have To
It’s no secret that organizations are seemingly dragging their feet when it comes to dedicating the time, people, and resources to preparing for the quantum threats to come. But when you consider the high amounts of stress and short tenures of most CISOs, it’s easy to see why they view quantum threats as things to put off until “later,” even though they’re not. Banco Santander’s Garcia says that there’s a growing need for a change of mindset and approach.
In his presentation on Comparing Strategies for Quantum-Safe Cryptography Adoption in Organizations, Garcia cited research from KMPG and Germany’s (BSI) that shows the overwhelming majority of CISOs are waiting to take any real action until there are standards (89%) or regulatory requirements (96%) in place that force their hands. People are burned out on the “sky-is-falling” messages they’ve been hearing for decades.
“People are going to act when they’re required to act. My conclusion is that risk-based messages do not work. They have not worked so far, and they will not work because we are talking about a threat that happens far in the future. So, we need to explain in a different way why things need to be done now.”
So, what’s the alternative? Garcia pointed to an executive action that came out of the U.S. White House as an example (a memorandum on “Migrating to Post-Quantum Cryptography”). The document breaks down specific requirements that must be met within set periods. For example: “Within 30 days of the memorandum, agencies will designate a cryptographic inventory and migration lead for their organization.”
The point is to create a sense of urgency and to show a way forward by outlining the preparatory steps that must be outlined within a limited period.
Consider the high levels of stress amongst CISOs for all of the urgent items on their to-do lists that have short timespans. It’s understandable (in some ways) why quantum preparations aren’t at the top of the list. After all:
- 94% of CISOs admit to being stressed at work, and 65% say it compromises their job capabilities;
- Three in four (77%) CISOs admit that job-related stress is taking a toll on their physical and mental health; and
- CISOs are in their roles for a median period of 4 years — meaning they’ll be out of their roles significantly sooner than quantum computers are expected to arrive.
7. Take a Stealth Approach to Get Funding and Support of Your PQC Initiatives
One of the key challenges I’d mentioned earlier when organizations face when planning for and implementing PQC-focused initiatives is that they often lack the financial support of their boards and c-suite execs. Although CISOs and other IT/cybersecurity professionals largely agree that quantum cryptography represents an opportunity to invest in new technologies and divest legacy systems, many of their organizations’ leaders don’t necessarily share that same opinion when it comes to supporting PQ initiatives with the companies’ checkbooks.
“Many organizations are struggling to justify a project with no end date. Most projects have a compelling event: ‘I have to go live by January 2024.’ PQ’s different. We don’t know when we don’t have to be live; we know roughly that we have to be ready by, probably, 2028, 2027 if we want to be a couple of years ahead of our adversary.
“[…] so if it’s that kind of timeline, try justifying that to a board member by saying ‘I think it’s near the end of the decade’ and they say, ‘well, this other project is going to generate us more revenue, reduce our risks more, and so on’ and they’ll put their money there.”
— Robert Hann, Global Vice President of Sales, Cryptographic Center of Excellence at Entrust
Even though boards often view quantum computing as a priority, protecting their organizations against quantum-based threats doesn’t seem to garner as much interest.
So, what’s the solution? Hann suggests taking a stealthy approach: start combining key aspects of your organization’s PQC initiatives into other more timely and profitable priorities your execs favor. For example, tie it in with your zero-trust strategy or AI strategy. Doing this helps the board set the goals and priorities they think matter most while enabling you to do what needs to be done to prepare for the quantum threats to come.
8. Businesses Want Financial Incentives to Become Early Adopters
One of the most interesting points discussed at the conference was brought up by one of the audience members during an open forum discussion by Anita Wehmann, Senior Advisor Information Security at the Ministry of the Interior and Kingdom Relations (BZK) of the Netherlands and Germain van der Velden: Being a “first mover” is a risky venture.
You’re bound to make mistakes that will cost your business money. If organizations and businesses are expected to take on the risks associated with being early adopters, shouldn’t there be some financial incentive(s) for them to do so?
“As this is such a global problem, there needs to be at least some clear incentive for ‘first movers,’” said the unnamed forum participant.
“I think we need to at least get some clarity on that – whether there will be possibilities to support each other also in the form of financial perspective. So, not only knowledge and things like that, but really, enterprises have a financial aspect as well. […] The financial part should not be forgotten if you want to enfold enterprises into this integration path.”
Regarding the concept of being an early adopter, Wehmann separately brought up an interesting point and question in a panel discussion near the end of the two-day conference: If the expectation from governments and industry leaders is that critical infrastructure organizations be among early adopters of PQC, isn’t that, in some ways, counterintuitive to critical infrastructure security?
Critical infrastructure organizations have a longstanding history of being risk-averse. But if those organizations are among the first adopters of PQC, then they’ll be the ones making the mistakes that could have potentially devastating results.
It seems to be a damned if you do, damned if you don’t kind of situation. But what’s the solution? As of right now, no one seems to have a definitive answer.
9. PQC Progress Requires Significant Collaboration Between Global Regions and Industries
Quantum readiness requires the best and brightest from around the world to come together for this shared cause. There have been significant collaborations between various agencies and research institutes across Europe, as well as with North America (U.S. and Canada). But even with those collaborations, there are different perspectives in terms of how we should approach this overarching goal, and even which algorithms should be used.
While many presenters agree that there’s already good collaboration going on between different countries’ cryptographic experts, there’s always room for growth and improvement. We need to connect more, coordinate better, and share more information.
Every initiative is valuable and has its own merits. We agree on many points, but there are nuances where different countries differ in terms of prioritizations and approaches.

Final Thoughts on the Insights Shared at the PKIC PQC Forum
We hope that you’ve found this article useful. From a non-cryptographer perspective, it was interesting to hear the different perspectives and earnest discussions that took place. Although some of the presentations left me with more questions than answers — for example, the intricacies of lattice-based algorithms — it’s opened up a wealth of information and ideas that I (and possibly you) had not considered. Did you attend the conference (either in person or remotely, like me) and have additional takeaways to share? If so, we’d love for you to share them in the comments below!
[ad_2]
Article link
