[ad_1]
Brand impersonation attacks hit companies ranging from small businesses to giants like Microsoft and Facebook. Explore what these types of attacks are and how you can protect your organization and customers
What do Microsoft, Facebook, and Crédit Agricole all have in common? Sure, they’re all big-name companies, but something else they share is that their brands are the three most commonly used in brand impersonation scams. These cyber attack scams involve someone pretending to be your company.
It’s said that imitation is the sincerest form of flattery, but that doesn’t hold true with brand impersonations. In these scenarios, bad guys use your name and reputation to swindle customers out of their login credentials, other sensitive data, and hard-earned money. But it may surprise you to know that your company isn’t a target in this situation. The target (i.e., the victim in this case) is the customer or other potential user who receives the deceptive communications and falls for it. Your company is simply a means to an end to help bad guys reach their true goals.
As you can imagine, mass brand impersonations result in significant costs and lost trust for those affected brands. The Federal Trade Commission (FTC) reports that the reported costs of business and government impersonation scams increased 85% year over year, bringing total losses from October 2020 to September 2021 to a whopping $2 billion! (This doesn’t include costs of impersonation scams that have gone unreported — and who knows how many of those have gone on that the FTC just doesn’t know about!)
But what exactly is brand impersonation? And, more importantly, how can you use digital identity to protect your brand and customers against these types of cyber attacks?
Let’s hash it out.
What Is Brand Impersonation? A Look at Brand Spoofing
Brand impersonation, or brand spoofing, is a phishing tactic that involves cybercriminals falsely representing themselves as your organization or one of its employees. This is typically done to get people (e.g., your customers or other users) to believe they’re interacting with your company. This way, they’ll be more willing to share their personal or otherwise sensitive information.
You know those fake Walmart or Amazon emails you always get in your junk mail? Yeah, those are just two examples of the types of mass brand impersonation you’ll commonly see nowadays. The idea is to get you to click on a link that takes you to a fake login portal where you’ll be prompted to provide sensitive information such as your username and password. Since this phony site is controlled by the attacker, they’ll be able to steal your login credentials or other information easily.
Brand impersonation attacks are often a shotgun “spray and pray” approach wherein an attacker sends out mass emails to a bunch of people with the hope that at least a few will fall for them. Bad guys ride the coattails of the trust your company has established with customers to trick them into doing one or all of the following:
- Logging into a fake account portal that enables the attacker to steal their login credentials
- Making payments for fraudulent products or services
- Providing other desired sensitive information
- Installing malware onto their devices
But what do some of these brand impersonation emails look like? In truth, you’ve probably already received some and just didn’t know it. Let’s take a quick look at a couple of brand impersonation scam emails I’ve received in the past few months.
A Look at Real-World Brand Impersonation Scams
I frequently receive fake Norton LifeLock and Microsoft emails — almost daily, in fact. Suppose I was a legitimate Norton LifeLock customer and wasn’t paying attention to the sender’s email address. In that case, I might not notice that an email came from an unrelated domain. As a result, I might wind up handing my username, social security number, or other sensitive information over to a cybercriminal on a silver platter.
Here are a few examples of Norton LifeLock phishing emails I’ve received:
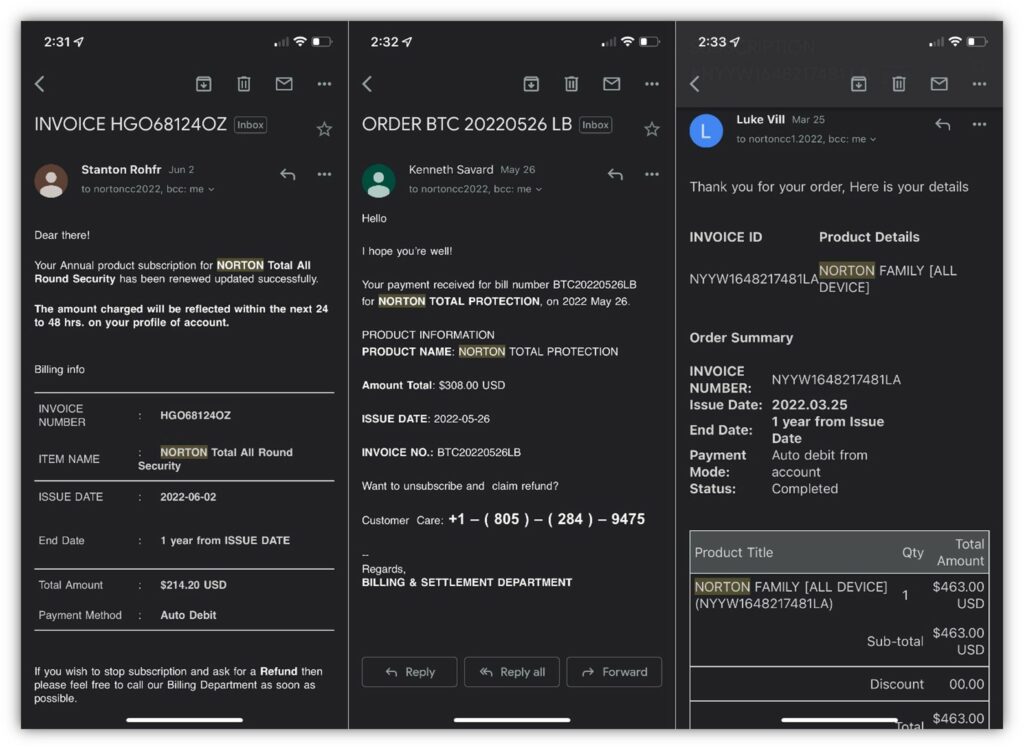
Image caption: A side-by-side screenshot of three Norton LifeLock scam emails I’ve received.
Look at all of the different invoice numbers and amounts, ranging from $214 to $463. Notice that the emails are all sent to me using the BCC field instead of including me as the only email contact. All of these factors, coupled with the fact that the senders’ email addresses have nothing to do with Norton and the messages are super generic, help me recognize that these emails have “phishing” written all over them.
Common Brand Impersonation Scams and Attack Vectors
Brand impersonation attacks can occur in many ways. Attackers often create emails, text messages, social media profiles, and/or websites that look like they’re from a legitimate brand to win the trust of their targets.
A few of the most common organization or brand impersonation scams you’ll find include:
- Tech support scams — These scams often involve an attacker coercing a victim into downloading malicious software onto their devices under the false premise that their device is infected with malware. FBI data shows that 23,903 tech support fraud complaints were received in 2021 with losses surpassing $347 million.
- Vendor scams — Not all targets are consumers. In some cases, attackers will impersonate one business in order to target another. In these cases, cybercriminals will create fake invoices that they send via email to trick the target organization’s employees into clicking on it and installing malware. Sometimes, they’ll go as far as to create fake websites and domains that closely resemble the real organization’s website to trick the victim into visiting it.
- Subscription scams — Here, attackers convince unsuspecting users that they’ve been charged for services or products. To get a refund, they must call a call center or download some type of software. (Think of the Norton LifeLock scam we talked about earlier.)
- Law enforcement scams — Bad guys have no shame. Many cybercriminals have no qualms about pretending to be someone at your local police station or even impersonating a federal agent. Here, they’ll threaten targets with fines or even prison if they don’t comply with their demands.
- Job offer/recruitment scams — Yes, truly, nothing is sacred. Whether you’re unemployed or are just looking for a new position, beware of fake job recruiters. These are among the lowest-of-the-low scammers who prey on individuals; they make false promises of great jobs to lure them into sharing sensitive information.
4 Methods of Brand Impersonation Attacks (and How to Tell They’re Scams)
Let’s explore a few examples of the most common ways cybercriminals carry out these attacks:
1. Email Mass Brand Impersonation Attacks
This is a favorite approach for many cybercriminals because emails are cheap, quick, and easy to send. But what makes them particularly attractive is that they can simultaneously use these electronic messages to target many potential users. Cybercriminals can send out emails from domains that look similar to yours to trick users into providing info, opening malicious attachments, or going to phishing or malicious websites. This approach doesn’t require that they have access to your account (such as in an account takeover [ATO] attack — more on that in a second).
Let’s consider the following example of a brand spoofing email I received that was targeting American Airlines customers:

Image caption: A screenshot of an American Airlines phishing scam email I’d received.
Overall, this phishing email is pretty well put together. The grammar is pretty good, the graphics look official, and the display of “American Airlines” as the sender is a nice touch. However, if you dig a little deeper, you’ll start to notice a few key points that give away this is a spam email.
First, let’s start with what the sender’s email address actually looks like when you go beyond the surface:
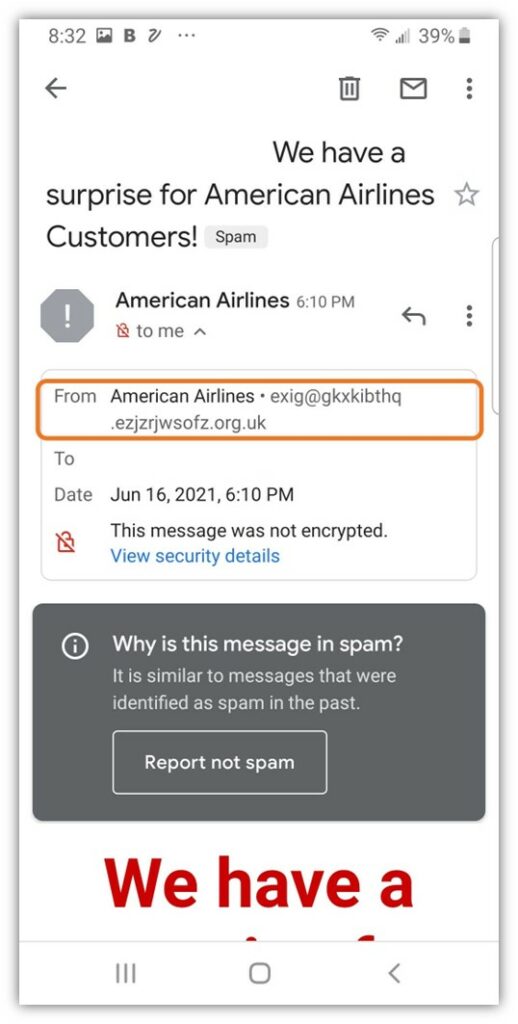
Image caption: An up-close screenshot that showcases the sender’s non-American Airlines email address.
Next, let’s look at the URL that the OK button is trying to direct me to:
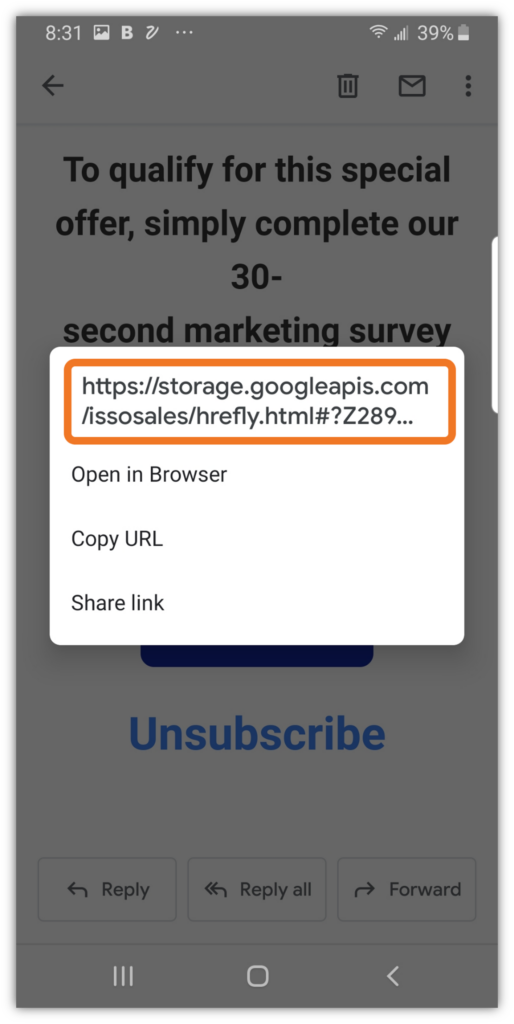
Image caption: An up-close screenshot that showcases the non-American Airlines URL that the button tried to direct me to click on.
That part doesn’t look very official, does it? Definitely not. And it’s important to note that Googleapis links are commonly tied to phishing scams and are used to distribute malware. This means that if I end up clicking on the link, it could result in malware being installed onto my phone or computer. Yikes.
Let’s consider another example that, in some ways, is a little trickier. It comes from what appears to be a legitimate email account and domain. This may have been a case of an account takeover attack, which means that an attacker gained access to a legitimate email account and used it to send out phishing or malicious messages.
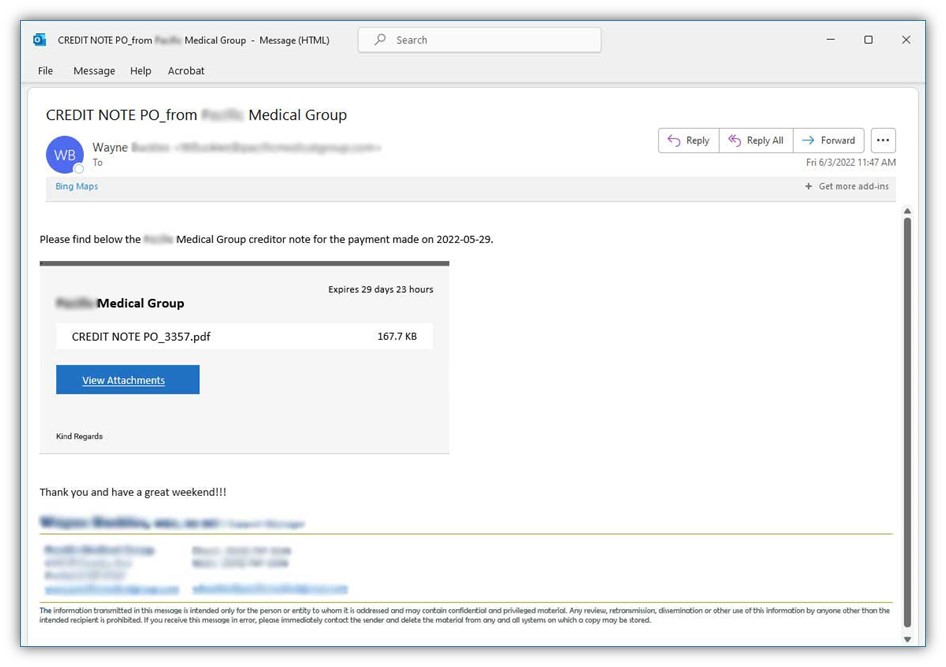
Image caption: A screenshot of an email I received containing a fraudulent (and potentially malicious) PDF attachment.
The first glaring issue here is that I don’t do business with this organization, nor am I one of their patients. Second, let’s take a closer look at a link that was embedded in the View Attachments button:
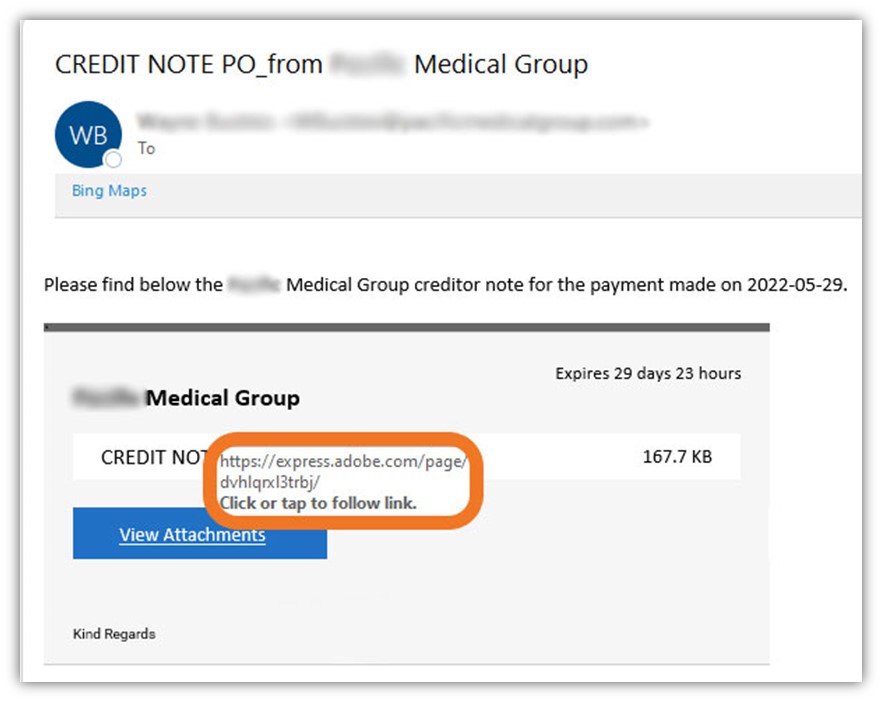
This link would take you to an unknown website URL that is designed to appear to come from Adobe. But not everything is as it appears; when I checked this link against VirusTotal’s search tool, the search result shows that it’s flagged as malicious:
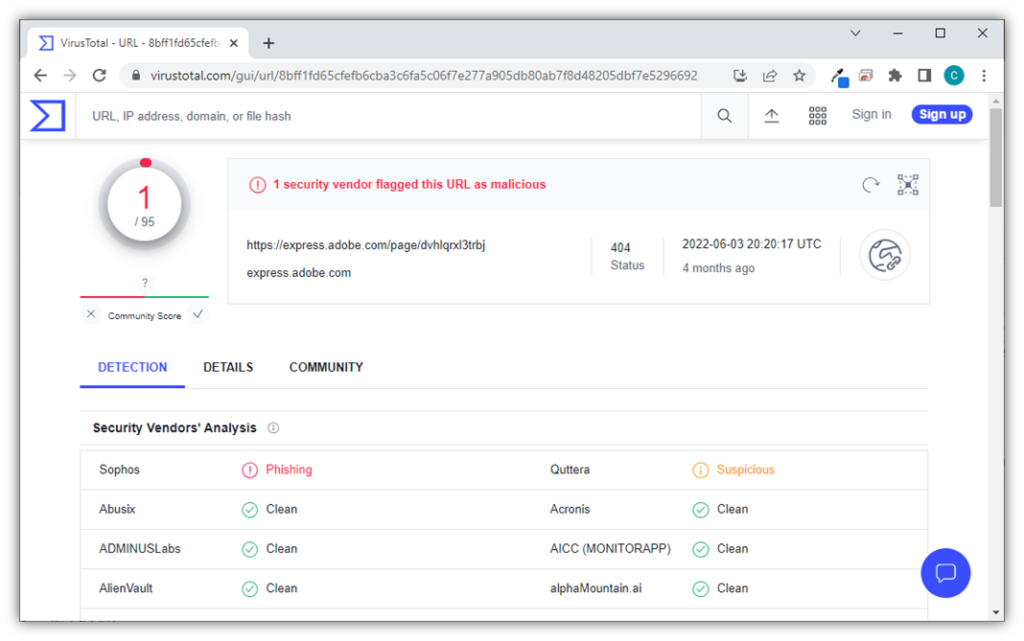
Image caption: A screenshot of the URL checking results of the suspicious emailed link.
Yup, it’s always a good idea to do a secondary check before clicking on any unknown (and unsolicited) links. Clicking on this link opens you up to the risk of getting malware onto your device or going to a phony login portal that can steal your username and password.
2. Brand Impersonation Phone Calls
Cybercriminals use voice phishing (vishing) to carry out attacks. In this case, bad guys use phones (often with the help of automated dialers) or VoIP systems to call people while pretending to be well-known companies or organizations. Some common examples of vishing scams involve personating the following companies or agencies:
- Technology companies,
- Financial institutions, and
- Law enforcement and other federal agencies (such as the FBI or IRS).
Bad guys know that fear is a big motivating factor. This is why some threat actors love to use scare tactics to coerce or manipulate victims into doing something they normally wouldn’t (like handing over account information or other sensitive info).
3. Brand Impersonation SMS Text Message Scams
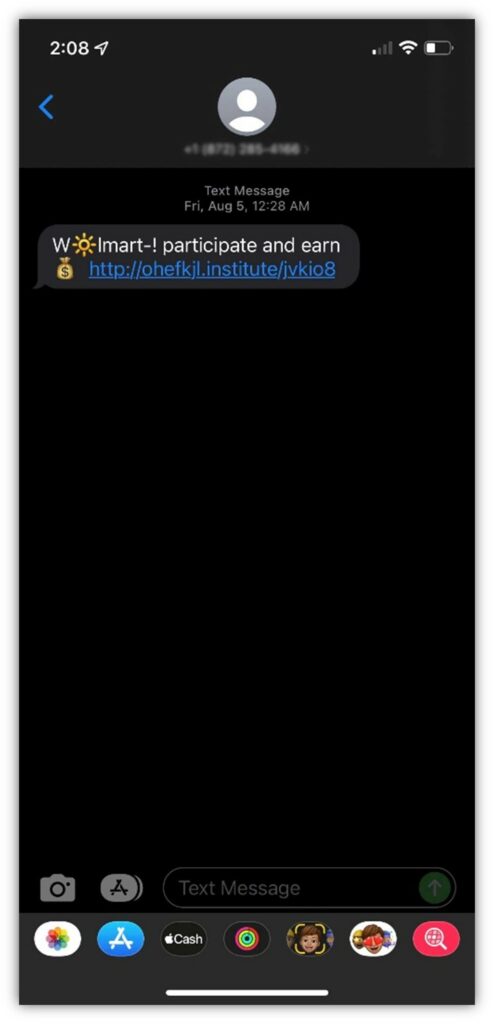
SMS phishing, or smishing, is an approach cybercriminals use to drive targets to phishing or malicious websites. They send SMS text messages containing links to websites (under the guise of enticing surveys, sweepstakes, or free gift card offers) to random or targeted users’ phone numbers to see who will bite. An example of such a text message is the screenshot displayed to the right.
The goal here is to trick victims into believing that the messages are legitimate. This way, they’ll be more likely to click on the link in the message, which can lead to a fake login portal or a site with drive-by downloaders.
4. Some Cybercriminals Combine Multiple Phishing Methods
Some brand impersonation attacks involve a combination of different attack methods. For example, I’ve received Microsoft subscription scam emails wherein the attacker says I’ve been charged for a phony recurring subscription. To cancel it or get a refund for the charges, I’m prompted to call a phone number where they can walk me through downloading a remote desktop protocol (RDP) application that will give them access to my device.
The attackers use the excuse that I need to download the program to connect to their bank server to initiate a money transfer to my account for reimbursement. Of course, the truth is that the whole situation is utter nonsense: there is no refund, as the charge wasn’t real.
The attacker’s goal is to get me to give them remote admin access to my device so they can:
- Install malware,
- Steal my information,
- Encrypt my files, or
- Do other nefarious things.
Needless to say, if I fall for even one of these scams, it’s bad news for me and will likely result in a payday for the attacker.
Mass Brand Impersonation Enables Cybercriminals to Capitalize on Your Reputation
If you’re like most organizations, you’ve worked long and hard to establish your business. You’ve probably spent many long days, nights, and weekends trying to win over customers and prove your value as a reputable organization they can trust. All your hard work goes out the window when someone hijacks your good name and uses it to cause harm through mass brand impersonation attacks and scams.
Attackers use phishing and other social engineering tactics to make their phony emails, text messages, and/or emails appear legitimate. To help prevent some of the usual attack vectors and help strengthen your brand against these types of attacks, it’s crucial that you take steps to secure your digital identity.
What Is Digital Identity and Where Does It Come Into Play?
Your digital identity is what helps people know you’re really you in the digital world. It’s a combination of various verifiable identifying data that offers assurance to others that you or your organization is legitimate and not an imposter.
An easy-to-recognize example of digital identity is an organization validation (OV) or extended validation (EV) SSL/TLS certificate. This digital certificate file ties key organizational information to your domain — verifiable information such as your common name and locality information — and is a key component of public key infrastructure (PKI), which we’ll speak to in just a few moments.
When you install an EV SSL/TLS certificate on your web server, it communicates to users’ browsers that your website is legitimate and displays your verified organizational information upfront. Here’s a quick example of how that looks on our website:
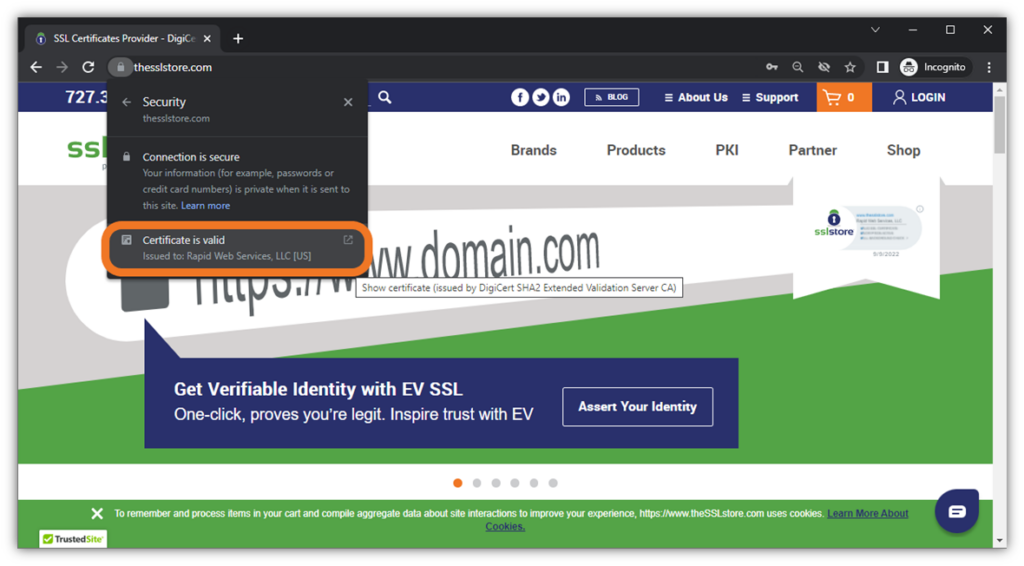
How to Protect Your Digital Identity Against Use In Brand Impersonation Scams
Now that we know what mass brand impersonation is and why it’s such a problem, there’s only one big thing left to talk about now: what you can do to prevent these impersonation attacks from affecting your organization.
Public key infrastructure (PKI) — essentially, the backbone of internet security — relies on the use of PKI digital certificates. These certificates come in multiple varieties and serve different purposes. Here are some of the ways that you can protect your brand online using PKI and other methods.
Secure Your Domain with an EV SSL/TLS Certificate
Installing an extended validation (EV) SSL/TLS certificate ensures you’re asserting your digital identity in the biggest way possible. An EV certificate ensures your company’s verified name displays as prominently as possible while also including more detailed organizational information in your certificate details.
You may also want to consider registering domains that closely resemble yours and install redirects to your main site to keep cybercriminals from registering those domains and doing anything bad in your name.
Use Email Signing Certificates to Add Your Signature to Outbound Emails
Much like how monarchs and others throughout history used wax seals to authenticate their correspondences and ensure their integrity, you can use a special digital certificate (called an email signing certificate) to do the same with your emails.
Digitally signing your emails is the modern solution to an age-old problem of communicating securely with someone when you’re physically not in the same location. Using a cryptographic signature provides a way for your email recipients to verify that your messages are authentic and haven’t been altered.
Protect Your Domain Against Unauthorized Usage by Setting Up DNS Records
Set up domain-based message authentication, reporting, and conformance (DMARC) records on your domain name system. This builds on the sender policy framework (SPF) and domain keys identified mail (DKIM) and helps to ensure that only authorized users can send emails on behalf of your organization’s domain. DMARC is also a requirement of BIMI, which we’ll speak about next.
Show Customers Your Emails Are Legitimate Before They Even Click on Them with BIMI & VMCs
Implementing brand indicators of message identification (BIMI) in combination with using verified mark certificates (VMCs) adds another layer of digital identity to your outbound emails. This allows you to brand your mail right in recipients’ inboxes. This way, recipients know your emails are legitimate just by looking at your verified logo next to your messages in their inbox.
Apple and Google support using BIMI and VMCs to display your verified logo in emails received by users on their respective platforms.
Assert Your Digital Identity in Your Code to Secure Your Software & Supply Chain
If you’re a developer or publisher, this is for you. Digitally signing your software, patches, scripts, and other executables using a code signing certificate enables you to prove their authenticity to browsers and operating systems. This process attaches your verifiable digital signature to your code using cryptographic functions showing that your products haven’t been altered since they were originally signed.
Doing this assures your users that your software is legitimate and hasn’t been modified without your knowledge.
Of course, it’s important to note that these certificates won’t stop attackers from simply claiming to be you and delivering unsigned code. However, what they do is provide users with a way of determining whether your communications, website, or software are legitimate. This way, if they download software or receive an email from “your company” (i.e., an attacker) that’s not digitally signed or doesn’t contain your verified logo, it’ll give them a reason to pause.
Train Your Employees to Recognize Authentic Company Communications
Educating and training your employees about cybersecurity is crucial for helping them keep your organization safe. If your employees have no clue as to how to identify a legitimate email from an imposter’s fake one, then you might as well post a sign out front stating, “cybercriminals — make yourselves at home.”
As part of the training you provide, you’ll want to educate your employees to recognize and decipher your legitimate communications quickly and easily. This way, they can quickly assess messages to figure out whether they’re authentic. A well-known example of a company that takes this approach is PayPal:
- Dedicates an entire section of their website to educating users
- Sends out emails regularly to their users, warning about scams and providing examples of emails to avoid
- Displays other messages to educate users of the dangers of brand impersonation and other phishing scams
Monitor Your Brand Online
Your work isn’t done yet. Another crucial step in preventing brand impersonation (or, at least, mitigating its impact) is keeping an eye on your brand name online. Look out for instances of how and where it’s being used and referenced by other parties. You can even set up Google Alerts to inform you any time someone publishes something relating to specific keywords or key phrases you enter — for example, your company’s name.
To set up Google alerts, check out this resource from Google’s Support page.
Keep Your Secrets Safe
We’re going to leave you with one final but important thought. For you to put your digital identity to use in an effective (and secure) way, you must properly manage your PKI certificate keys, passwords, and other “secrets.” If you don’t carefully manage your access information and even just one of them gets lost or stolen, you risk exposing your sensitive data and systems or someone signing things they shouldn’t in the name of your company.
Either way, the scenario will likely result in damage to your brand and reputation, fines, or maybe even lawsuits down the road. It’s just bad news all the way around with no upside.
To learn more about certificate management, be sure to check out our Certificate Management Best Practices Checklist.
[ad_2]
Article link
