[ad_1]
Industry leaders decided to hold off on rolling out the new secure key storage requirements for organization validation (OV) code signing certificates until June 1, 2023
Back in July, we published a blog post explaining that changes were coming down the pike to require standard code signing certificates’ private keys to be stored on approved hardware security devices. This rollout was supposed to take effect starting Nov. 15 (Nov. 14 for North and South American users). However, as things often go in life, the situation has changed (and continues to evolve).
The CA/B Forum has decided to postpone the deadline until June 1, 2023, giving certificate authorities and certificate users more time to update their systems and processes. Let’s take a quick look at what the changes are and why they’re being delayed.
Let’s hash it out.
A Quick Recap of the Proposed Changes to OV Code Signing Certificate Key Storage
We’re not going to go over all of this super in depth since we already have a full article on this topic. However, we thought it would be good to at least briefly cover the CA/B Forum’s new industry requirements for issuing and storing OV code signing certificates before getting into the changes to when it’s supposed to roll out.
- The CA/B Forum’s new requirements affect new/reissued IV and OV code signing certificates. The changes listed in the CA/B Forum’s Code Signing Baseline Requirements (CSBR) version 3.1 specify how to create, store, install, renew, and reissue corresponding private keys for individual validation (IV) and organization validation (OV) code signing certificates.
- Certificate signing requests (CSR) for code signing certificates go the way of the Dodo bird (for most users). Instead of you creating and submitting a certificate signing request (CSR) form for each certificate, your issuing CA will usually handle the certificate and key generation processes on their end. This is similar to the process for extended validation (EV) code signing certificates.
- The cryptographic module(s) (hardware) you use must meet specific security standards. Not just any secure hardware will work. You must use FIPS 140 Level 2/EAL 4+ compliant secure hardware cryptographic modules or signing services as a minimum to store your code signing certificates’ sensitive private keys.
All of these things aim to improve the security of your private keys. But if the changes are so positive, why are we delaying them?
Why These Changes Are Being Pushed Back Until June 1, 2023
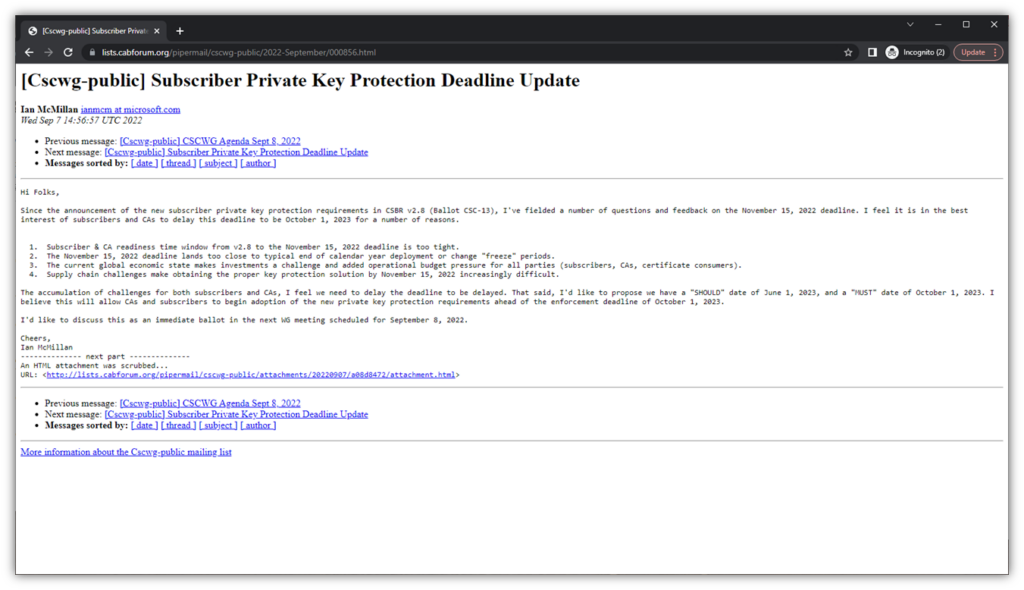
In a CA/B Forum public mailing list discussion, Ian McMillan, Principal Product Manager at Microsoft, explained that the deadline for the proposed changes was “too tight” for subscribers and CAs alike and that he’d received a lot of emails expressing concerns about the Nov. 15, 2022 timeline. While having an aggressive deadline is great, the issue is the requirements would be difficult to implement effectively in such a brief window.
In part, McMillan said there are concerns relating to the ongoing global supply chain challenges and rising costs. These factors make it difficult to get the necessary hardware security tokens en masse, particularly when you consider that Keyfactor reports that organizations have an average of 25 code signing certificates, yet only half (51%) store them in hardware security modules (HSMs).
Unsurprisingly, representatives from several CAs — DigiCert, Sectigo, and Entrust — agreed that delaying the change will be good for the CAs and certificate users alike. Because code signing is such an integral part of the software development process, certificate users have a wide variety of systems and processes that will need to be supported and/or updated. This gives them time to finalize their process and get their ducks in a row.
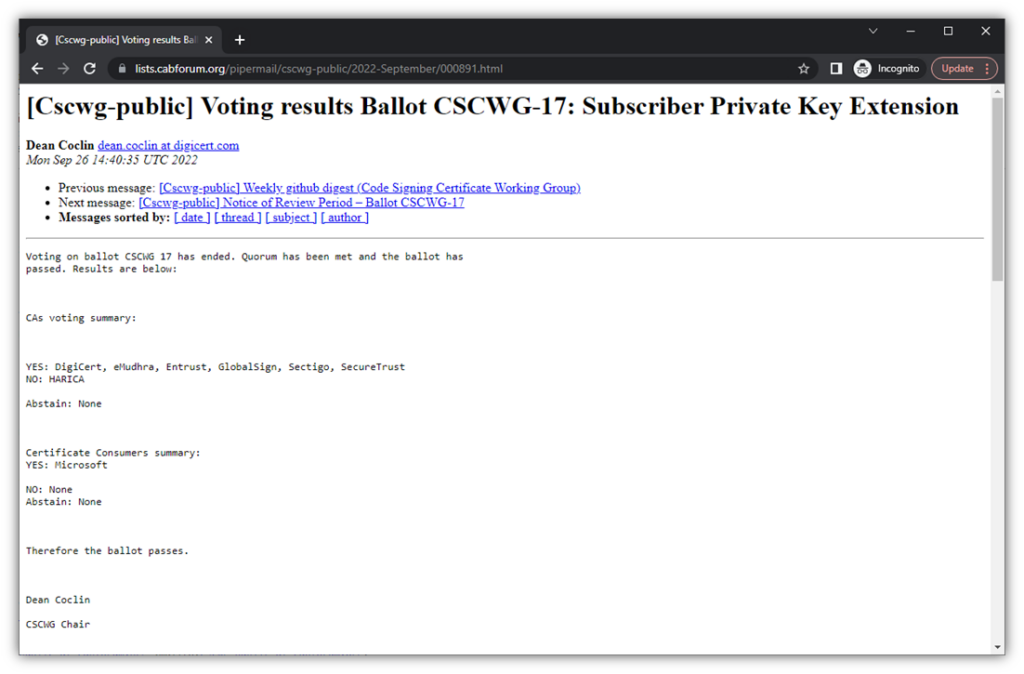
Here’s a quick look at the ballot voting results that were posted on the CA/B Forum’s CSCWG public discussion list:
Do I Have to Wait to Make the Key Storage Changes?
No. If you’re the proactive, go-getter type who wants to start implementing the changes right away, you can certainly do so if you have the appropriate cryptographic hardware. This way, you don’t have to wait and worry about doing so down the road. Reach out to your certificate provider to see what steps you need to take to make this happen.
If you’re like most companies that want to take advantage of the delay, that’s okay, too. But just be sure to give yourself ample time to make the changes before the planned June 1, 2023 deadline arrives.
[ad_2]
Article link
