[ad_1]
Virtually every day, there’s a new headline about some company falling prey to a data breach. We’ve asked 11 industry experts to share their insights on what every CEO needs to know regarding cybersecurity
Editor’s note: We’ve added insights from one additional industry expert.
Data breaches make news headlines virtually every day. But breaches are just one of many cybersecurity issues facing organizations — many things can go wrong, including outages and unplanned downtime.
The data backup service Veeam reports that cybersecurity incidents were the leading cause of outages for 15% of survey respondents. Of course, protecting your organization against cyber attacks is a significant issue. But this can be especially hard for organizations to do if they’re guided by leaders who don’t understand the threats and realities of creating and maintaining strong cyber defenses.
This is why we’ve decided to ask industry leaders what they would like for their CEOs to understand regarding their organization’s cyber defenses. These 11 leaders share their insights about what every CEO needs to know about cybersecurity.
Let’s hash it out.
11 Insights Your CISO, IT and Cybersecurity Pros Want You to Know as a CEO

As a CEO, you might get a lot of recognition and accolades when your company is succeeding. However, when things go wrong — say, you find yourself the target of a cyber attack and a subsequent data breach — it means you also take a lot of heat. Often times, the burden of bearing the responsibility of your organization’s missteps and its weak security defenses falls squarely on your shoulders.
While this spells bad news for you, the good news is that there are things you can do to help prevent this type of scenario from happening. If you’re like most CEOs, cybersecurity isn’t your main area of expertise — but that’s OK … just knowing a few fundamental security concepts can help you make the right decisions for your company. Let’s check out what our team of experts thinks you should know about cybersecurity to avoid becoming the next data breach headline.
1. No Organization, Regardless of Size, Is Immune to Cybercrime and Cyber Attacks
Did you know that 43% of small and mid-size businesses don’t have a cybersecurity defense plan in place? This data from BullGuard calls out a massive concern regarding small businesses and their perceptions of cyber threats.
For many businesses, small businesses in particular, their leaders believe that they’re not likely to be targeted by cybercriminals because they are too small. But this is a fallacy; Barracuda Networks reports that small businesses (i.e., those with 100 or fewer employees) are the targets of 350% more social engineering attacks than their enterprise counterparts.
Morshed Alam, a software developer and founder of Savvy Programmer, addresses this common misconception:
“CEOs need to be acutely aware of the fact that their organizations are always at risk of a cyberattack. No organization is immune, and even the most secure ones can be breached if hackers are determined enough.”
— Morshed Alam, software developer and founder of Savvy Programmer
Part of this understanding is knowing what types of risks they face and how those risks would impact their organization.
2. Cybersecurity Touches Virtually All Areas of Your Organization
CEOs typically see things from a 30,000-foot perspective. As such, they may not see the intricacies of how some specific aspects of business overlap can impact others. This is why it’s important that every CEO understands that cybersecurity isn’t just about protecting your systems against cyber attacks and cybercriminals.
As Alam also shares:
“CEOs also need to be aware that cybersecurity is not just an IT issue; it’s a business issue. If a company’s data is compromised, its customers could lose trust in it, its stock prices could plummet, and it could even face legal action.”
— Morshed Alam, software developer and founder of Savvy Programmer
3. Ask Your Staff to Communicate How Technical Items Impact Business Concerns
While this makes sense logically speaking, employees often find it difficult to convey these points to some CEOs. This is why one of our experts, Andreas Grant, a network security engineer and founder of Networks Hardware, says it’s important for employees to put things into terms you’ll understand, particularly how it helps you achieve your organization’s goals:
“My strategy is to translate the cybersecurity strategies into the language of CEOs. By this, I mean to convert an incident into the amount of money they might be losing. To show how many days it might take for the business to get back on track.
When your CEO knows the importance of cybersecurity and is in on the cybersecurity infrastructure plans, you can start picking your battles easily. Don’t expect to hand over a list of issues and be done with it as you do have to pick your battles one by one.”
– Andreas Grant, founder of Networks Hardware
It’s a smart move by your IT and cybersecurity employees to sort of “translate” things for you and spell out why it matters. However, the onus shouldn’t entirely be on them; it would also be beneficial for you take the initiative as well to familiarize yourself more with the importance and impact of cybersecurity investments within your organization.
4. Cybersecurity Should Begin When Your Organization Does
I think Chloé Messdaghi, Chief Impact Officer at Cybrary said it best:
“If you don’t have proper security in place, you don’t have a company. When security is not in-place from the very beginning of a company, you are opening the door for breaches to occur and when they do they will impact every aspect of your operation.”
— Chloé Messdaghi, CIO at Cybrary
Data from a 2022 IBM/Ponemon study shows that the average data breach costs companies $4.35 million. But that’s not the only cost you’ll face:
“In addition to direct financial costs and loss of your corporate and customer data, you lose customer trust. Many small and midsized businesses have gone out of business from a single data breach. The CEO must acknowledge that cybersecurity is a top priority early on.”
— Chloé Messdaghi, CIO at Cybrary
This is why cybersecurity should never be an afterthought; it’s something that should be planned for and implemented at the same time your organization launches.
Not having cybersecurity measures in place up front is kind of like opening a new brick-and-mortar storefront without bothering to install a lock or security gate on the front door. Sure, your business will run, but it may not do so for long. And if it does, you’re going to run into a lot of theft and crime-related issues as a result.
This is why Camila Serrano, Chief Security Officer at MediaPeanut, says that she wishes CEOs would start investing in cybersecurity from the get-go, right from when an organization is first conceptualized.
“What I have observed in many companies, most especially small businesses, is that the business plan rarely includes cybersecurity as an essential component when starting out and that it only comes as an afterthought when the business has already taken off. As a result of this, cybersecurity practitioners come in either too late or catching up to patch up systems and processes that might cause data leaks and security problems.”
— Camila Serrano, CSO, MediaPeanut
Create and Implement Proactive and Responsive Cybersecurity Plans to Increase Cyber Resilience
The concern here is that cybersecurity becomes strictly a reactive rather than a proactive approach. By not anticipating potential risks and having plans or solutions in place ahead of time, you’re at a significant disadvantage and are left scrambling to address situations as they’re happening.
A good way to combat these issues is to create business continuity, incident response, and disaster recovery plans. Nathaniel Cole, Chief Information Security Officer at Network Assured, shares the following:
“Spending time to develop playbooks or runbooks to respond to, both, routine and more complex incidents will expedite the ability to contain and minimize the impact of an incident. With proper runbooks or playbooks, it is possible to respond quick[ly] enough to stop the loss of data or exfiltration of data from the network. Without the investment in response to alerts, what could have been a non-issue can turn into a full fledge incident.”
— Nathaniel Cole, CISO at Network Assured
But creating these plans isn’t enough; you also need to regularly practice and test these plans to ensure they meet your needs (or update them if they don’t). Your policies should be living, breathing documents that you regularly review and update as needed. They should never be shoved in a drawer and only get pulled out when crap hits the fan. As Chloé Messdaghi reminded me, “An incident response protocol that is not well practiced is no plan at all.”
5. Cybersecurity Training Isn’t Just a Once-a-Year Kind of Thing

It’s no secret that you and your employees are the first line of defense against cyber threats. After all, they’re the ones that cybercriminals try to trick, manipulate or coerce into doing something that can hurt your business. No one is safe from becoming a cybercriminal’s next target and data from Verizon’s 2022 Data Breach Investigations Report (DBIR) shows that four in five (82%) of data breaches are linked to “human element” based vulnerabilities.
Peter Carroll, founder of The 2hO Network (a zero-trust networking and secure remote team enablement software company), is one of many experts who called out employees as a big vulnerability:
“The single most important factor in cybersecurity is the human. The most advanced equipment can’t protect you if your employees are unknowingly responding to phishing emails. Most data breaches are a result of social engineering.”
— Peter Carroll, founder of The 2hO Network
The best way to shore up your defenses is to educate employees about what threats exist and what they can do to keep your organization and data safe. This is why cyber awareness training should be required for every member of your organization, regardless of their rank, as well as other network users (such as contractors, interns and even board members). Global research from PwC’s 2022 Global Digital Trust Insights report shows that CEO and Board cyber awareness training is the most highly regarded way for improving cybersecurity.
6. Creating a Culture of Security Goes a Long Way in Making Your Organization More Secure
Creating a transparent, cybersecurity-oriented culture is crucial when it comes to improving the security of your organization. According to Nathaniel Cole:
“Without a culture of security, an organization can never truly address such a large project. Culture includes senior leadership conveying a sense of responsibility for securing assets and data. This includes following the policies and limiting exceptions to policies as much as possible.
Communicating on a frequent basis about how security is the full organization’s responsibility and setting clear expectations. This is not something that is a burden to the organization but something that is required for proper business to be conducted.
And lastly, if the organization is conducting phishing email attacks, if a leader gets caught, fess up to the organization to show that anyone can fall prey.”
— Nathaniel Cole, CISO at Network Assured
7. Your Team Needs to Have Complete Visibility of Your IT Infrastructure
Eslam Reda, founder of SECLINQ and head of cybersecurity services at Nueva Solutions, says that you can’t protect something if you don’t know the threat exists. No matter what shiny, expensive tools or software you use, they won’t do you any good if you don’t have a clue as to what the assets are you’re trying to protect.
Reda recommends starting off by creating and maintaining an accurate, up-to-date list of your digital and physical assets is a big step towards your goal of achieving end-to-end security.
“CEOs master the art of business planning, when it comes to cybersecurity it is the same. You have to think 10 steps ahead, understand the threats you might face, plan how will you protect your organization from these threats, and build an incident response strategy and a disaster recovery plan for when things go wrong.”
— Eslam Reda, SECLINQ founder and head of cybersecurity services at Nueva Solutions
An important part of maintaining complete visibility of your network and overarching cybersecurity infrastructure includes tracking and managing your public key infrastructure (PKI). This includes carefully managing your certificates and keys and knowing where each one is in use within your infrastructure.
Avesta Hojjati, Vice President of Research & Development at DigiCert, stresses the importance of understanding the ever-changing threat landscape while also keeping other basic security concerns in mind:
“Similar to knowing how the revenue has decreased or how burned out the employees are, the threat of having an old technology stack, untrained & unaware employees (specifically around the importance of cyber security), and forgotten code base Is something that CEOs should be constantly reminded and aware of.”
— Avesta Hojjati, Vice President of Research & Development at DigiCert
Hojjati says that part of having full visibility of your IT environment entails getting rid of the unknowns — unknown codes, certificates, and applications.
Knowing These Risks, and Understanding Your Tolerance of Them, Can Play In Your Favor
Some companies jump headfirst into using new software programs just because they’re perceived as the “latest and greatest” things. But nothing beats old school research and threat assessments when it comes to evaluating your organization’s risk tolerance and response capabilities. Nathaniel Cole cautions against chasing industry trends and adopting the newest technologies just because they’re shiny and new.
“There is no silver bullet to security[;] it requires investment, research, and assessment to operate in an efficient manner. Focusing on risk assessments and understanding the business risk tolerance can help with directing operational cost to the right controls and processes. This will help with showing tangible results in lowering exposure and impact of a security event.
With these results, it is possible to show executives and board members that the security team is being good stewards of the business and that when there is a request for additional spend or investment, it [has] been reviewed with some level of prudence.”
— Nathaniel Cole, CISO at Network Assured
8. Automation Goes a Long Way in Helping Your IT/Cybersecurity Team Focus On Critical Tasks
Purchasing big-ticket items that, on the surface, don’t appear to directly help you achieve your goals can be a hard decision for many CEOs. After all, it means that big chunk of money can’t be used for other priorities that’ll help you move the needle. It’s also not big and splashy, which makes it a little more of a tough pill to swallow.
But investing in the right tools and software can help you achieve your goals indirectly — like automation, for example, which helps free up your team to concentrate on tasks that require human intervention and critical thinking skills. Henning Horst, Chief Technology Officer at comforte AG, says that every CEO needs to have a holistic, well thought out strategy to secure their IT environments. Ideally, one that includes automation.
“Today, you need to secure a moving target, with services on-prem and in the cloud spun up and down as needed dynamically and automatically, and data flowing and being analyzed in ways not possible to imagine before. In line with that, typically the environments are way too complex and changing too rapidly for a person or team to keep up with it unless they are supported by some sort of automation.”
— Henning Horst, CTO at comforte AG
A few quick examples of great automation tools that improve your organization’s cybersecurity include:
- Security monitoring, alerts, and event management tools
- Digital certificate life cycle management tools
- Vulnerability scanners
- Penetration testing tools
Camila Serrano emphasizes the importance of investing in the right tools:
“As security personnel, we have observed that executives have been working to better match their investment with the commercial value of the devices and data they are guarding for many years. However, given the recent wave of expensive threats and assaults and the accelerated speed of digital corporate change, it is more important than ever to focus on cybersecurity investments.”
[…] executives should already start automating often repetitive processes so that security personnel get to focus more on important data and property that needs full focus and protection.”
— Camila Serrano, CSO at MediaPeanut
9. Strong Cybersecurity Is More Than Just Having the Right Tools in Place
While having the right tools and technologies is important, they’re not enough on their own to keep your organization and data secure. Matthew Aubin, Technical Investigation Specialist and founder of CSCT Global says that cybersecurity isn’t just about having the right technology:
“There are many risks and threats in the business world, and it is crucial for CEOs to understand how to mitigate them. When it comes to cybersecurity, CEOs should be able to identify the threats as well as create policies and processes to minimize the risks. Some CEOs are not as tech-savvy as they should be, so it is important for them to be educated on cybersecurity practices.”
— Matthew Aubin, Technical Investigation Specialist and founder of CSCT Global
Earlier, we touched on the importance of having business continuity and disaster recovery plans in place. However, there are other plans and policies you should have in place as well, including a well thought out and updated cybersecurity plan.
But having the right plans, policies and procedures isn’t enough, either…
You Also Need to Have the Right People in Place
Being CEO doesn’t mean you’re omniscient. You don’t — and can’t — know everything there is to know about IT and cybersecurity. And, frankly, it’s not your job to know all of these things. This is why Wojciech Syrkiewicz-Trepiak, a Security Engineer at Spacelift (an infrastructure-as-code [IaC] platform for DevOps engineers), says that it’s imperative for CEOs to have the right culture and people in place to support it.
“The CEO is not obligated to understand the technical details but knowing how to direct those with the responsibility is their primary duty. It’s one thing to lead the IT team to compile the list of the company’s assets, keep it up to date, and put necessary policies in place. It’s another thing for the CEO to be able to answer the questions such as Who has access and levels of sharing? Or What data do you store, how do we classify them, and where is it?
The number one priority for the CEO is to have a dedicated security person like CSO to create an effective cybersecurity culture in the company. Cybersecurity culture in the workplace combines the employee[s]’ understanding of its importance and, most importantly, the risks while being motivated to put their two cents in to improve it constantly. It lets employees know how to respond or report such risks and creates a strong line of defense against cyberattacks or data breaches.”
— Wojciech Syrkiewicz-Trepiak, a Security Engineer at Spacelift
10. Compliance Alone Isn’t Enough to Ensure Your Organization & Data Are Secure
Compliance is key and ranked as the No. 1 cost factor for data breaches in IBM’s 2021 Cost of a Data Breach report. In this year’s report (2022), IBM’s data shows that the average cost of a data breach for organizations with the “highest levels of compliance failures” was a whopping $5.57 million. This data was collected between March 2021 and March 2022.
Horst says CEOs often view the relationship between cybersecurity and compliance in a singular way:
“Many CEOs still seem to treat cybersecurity mostly as a cost factor, something they have to spend money on in order to avoid steep fines associated with compliance standards like GDPR or CCPA. While compliance is an important factor, cybersecurity done properly can be a real business enabler and competitive advantage in order to generate more revenue and thus increase the overall value of the company.”
— Henning Horst, CTO at comforte AG
While achieving compliance is great, there’s more required to achieve strong cybersecurity. Nathaniel Cole says that while being compliant with industry and regional regulations is important, it doesn’t mean that your organization is fully secure against cyber threats and cyber attacks.
“One of the biggest items that seemed to always be a roadblock for many CEOs is that the company and security team attained certification (PCI, ISO, SOC2, etc.) and the assumption was that from that point forward the organization is secure. Sadly, compliance does not mean security, especially in the current environment of ever-evolving security threats.
Compliance shows that the organization has devoted the time to building a formal set of policies and processes to support a cybersecurity program but it often does not show all of the control gaps or risks that need to be addressed. I wish more CEOs understood that security is not stale, it is a constant moving target. Organizations need to assess, calibrate, and redeploy security controls and capabilities to close newly detected or newly emerging threats.”
— Nathaniel Cole, CISO at Network Assured
11. You Can Learn From Cyber Attacks Against Other Organizations
It always sucks to see other organizations fall prey to cyber attacks and ransomware. The silver lining, however, is that you can use these attacks as learning opportunities to improve your company’s cyber defenses.
Considering that the U.S. leads the way with the most cyber attacks in multiple categories — for example, 421 million ransomware attacks (according to SonicWall) and more than 60% of all phishing attempts (according to Zscaler) — there are, unfortunately, plenty of “learning opportunities” to choose from.
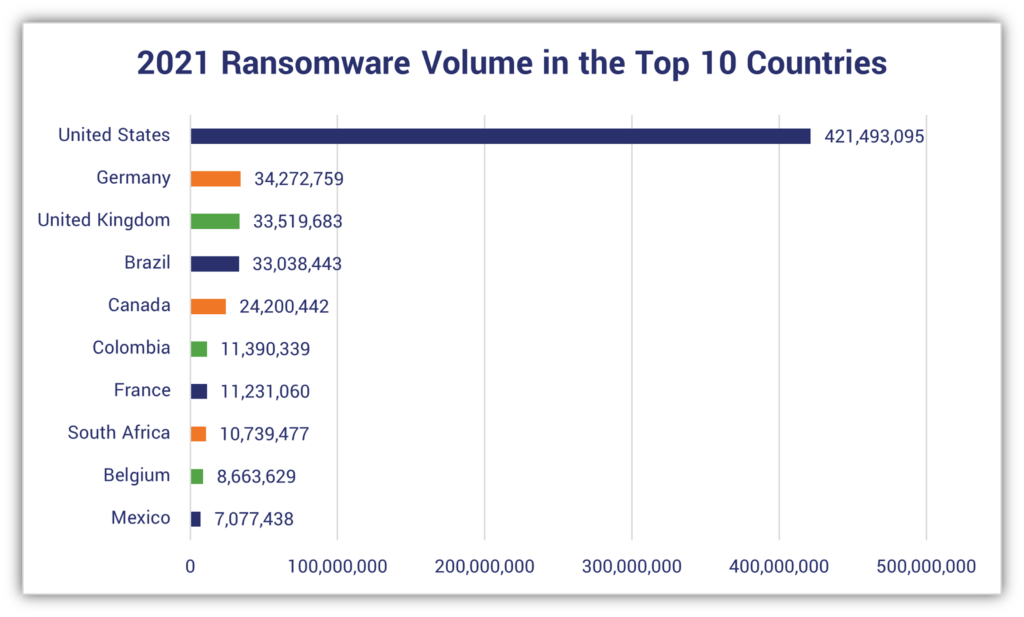
This is why Peter Carroll says it’s crucial that CEOs and organizations think like cybercriminals and investigators. “Investigate the attacks that are regularly in the news. Ask what would happen if that attack had targeted your organization. Then adjust your policies and educate your people.”
Get to Know Our 11 Experts
Morshed Alam is founder and editor of Savvy Programmer. Alam is a software developer with more than 10 years of experience working in the IT industry.
Matthew Aubin is a technical investigation specialist and founder of CSCT Global. Matt has more than a decade of experience relating to privacy, cyber security and electronic counterintelligence. He’s a cyber forensics expert who has worked with in partnership with local and federal law enforcement agencies as well as dozens of elected legislators.
Peter Carroll is the founder of The 2hO Network, a software company that specializes in secure remote team enablement and zero-trust networking.
Nathaniel Cole is the Chief Information Security Officer at Network Assured. With more than 15 years’ experience building & operating modern security programs under his belt, he uses these insights to write a cybersecurity advice column for business leaders on the company’s website.
Andreas Grant is a Cisco-certified network engineer and founder of Networks Hardware.
Avesta Hojjati is Vice President of Research and Development at DigiCert. Hojjati holds a Ph.D., Master of Science and Bachelor of Science in computer science. His research focuses largely on security and privacy, and he’s a member of the International Association for Cryptologic Research (IACR).
Henning Horst serves as Chief Technology Officer at comforte AG, a German tech company that offers software-based data protection solutions. Horst is a researcher and inventor who has worked previously as a systems architect and systems analyst.
Chloé Messdaghi is the Chief Impact Officer at Cybrary. Messdaghi has served as a chief strategist for Point3 Security as well as the head of security researcher community at Bugcrowd.
Eslam Reda serves as the founder of SECLINQ and head of cybersecurity services at Nueva Solutions. Reda has worked as a penetration tester, security engineer, researcher and consultant, among other roles, and holds many industry certifications.
Camila Serrano is the Chief Security Officer at MediaPeanut. She previously worked as a security analyst.
Wojciech Syrkiewicz-Trepiak serves as Security Engineer at Spacelift, an infrastructure-as-code (IaC) platform for DevOps engineers. He’s certified as both an information systems security professional (CISSP) and Offensive Security Certified Professional (OCSP).
[ad_2]
Article link
