We all know that cybercrime is on the rise. But there’s a lot more we can learn from cybercrime statistics — here are 23 cybercrime stats and practical takeaways.
Oh, boy. It’s been a while since we’ve published a heavy-hitting cyber crime statistics article. We didn’t publish one in 2021 — so, as the saying goes: there’s no time like the present!
Cyber crime as a whole has been steadily increasing since 2019 when we published our last cybercrime statistics article on the topic. This should come as no surprise, considering that the world has been entrenched in the throes of the Covid-19 pandemic and the skyrocketing scams and attacks that accompanied it.
In this article, we’ll dive into what constitutes cyber crime and go over some of the most notable cyber crime statistics and trends for 2021. We’ll also dive into some of the trends and stats the experts are pointing to for 2022 and the next few years to come. Note: This article is one that we’ll periodically update with new cybercrime stats
Let’s hash it out.
What Qualifies as a “Cyber Crime?” A Quick Cybercrime Overview

To be frank, the term “cyber crime” can be used to describe a wealth of different types of cyber-related security incidents and activities. For example, here’s a quick-hit list of some of the most common types of cyber crimes that you’re likely familiar with:
- Ransomware attacks and other malware attacks
- Data compromise (theft, loss, or manipulation)
- Account compromise
- Identity theft or fraudulent impersonations of individuals, companies or other entities
- Cryptojacking, crypto mining, and other digital currency scams,
Of course, there are many other types of crimes that count as cyber crimes that fall outside of this brief list. However, rather than go through the process of listing every single type, we thought it best to jump right into the cyber crime statistics (2021 and 2022) you’re here to read.
Cyber Crime Statistics: Cyber Crimes Are Profitable for Bad Guys, Costly to You
Cyber attacks and other types of cyber crimes result in serious costs for businesses. In some cases, these can be catastrophic losses that cause irreparable harm to the affected organizations.
Unfortunately, as a 2018 data analysis from Third Way shows, “less than 1% of malicious cyber incidents see an enforcement action taken against cybercriminals.” In other words, bad guys are getting away with essentially 99% of their nefarious activities without law enforcement doing anything in response to it. There are many potential reasons for this — such as a lack of cooperation between different organizations, jurisdictional differences, etc. — but the end result is that bad guys get to do bad thigs basically with near impunity. And your organization and customers are the ones who suffer the consequences.
With this in mind, this first cybercrime stats section will explore some of the biggest financial consequences worth noting.
1 — Data Breaches Come with an Annual Average Price Tag of $4.24 Million
It’s no secret that data breaches are costly events for businesses and other organizations. (This is why it’s first up on our list of notable cyber crime statistics.) In their 2021 Cost of a Data Breach Report, IBM shares that breaches that occurred between May 2020 and March 2021 cost an average of $4.24 million. This is up 10% from the $3.86 million reported in the previous year’s report.
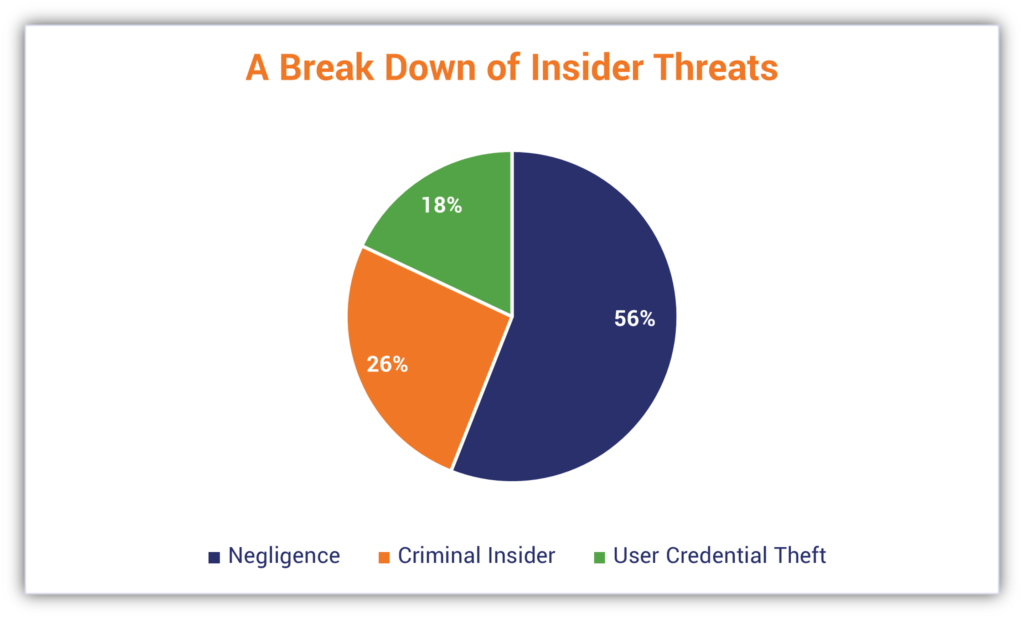
2 — $15.4 Million Is the Average Annual Cost of Insider Threat-Related Security Incidents
Data from Proofpoint’s 2022 Cost of Insider Threats Global Report shows that insider threats represent a growing risk area for organizations around the world. The report, which is based on a study of 6,803 insider-related incidents and was carried out by the Ponemon Institute, indicates that these events involved one of the following:
- 56% involved negligence
- 26% involved a criminal insider
- 18% involved user credential theft
3 — Threat Actors Enjoy $1.5 Trillion in Annual Cybercrime Revenues
Whoever said crime doesn’t pay clearly didn’t look at Atlas VPN’s research on estimated cybercrime revenues. The company’s researchers say that activities taking place on the dark web and via other illicit online markets generated $860 billion in earnings for bad guys. The second most profitable sector? Trade secrets and intellectual property theft come in swinging with estimated revenues topping $500 million.
4 — GDPR Fines Top €1 Billion in 2021, Dwarfing All Previous Years’ Combined Total Fines
The cost of cyber crime can be felt in other areas of your organization: noncompliance fines and penalties. One of the priciest regulations in terms of fines is the European Union’s General Data Protection Regulation (GDPR). In 2021 alone, GDPR fines reached a staggering €1,065,071,470, according to Atlas VPN’s research team!
Amazon received a €746 million fine (i.e., roughly $831 million) in response to GDPR privacy violations, according to the company’s June 30, 2021 SEC filing. Simply put, if your organization isn’t as secure as it should be, or if you’re not crossing your T’s and dotting your I’s when it comes to staying compliant with industry and regional regulations, then you might find yourself facing staunch penalties or fines.
5 — Cyber Security Incidents Cost Businesses an Average of Nearly $1.8 Million Per Minute
Yikes! According to RiskIQ, which was acquired by Microsoft in 2021, the average cybersecurity incident costs an average of $1,797,945 per minute! This means that cybercrime costs the same amount of money it would take to buy LG’s new 325-inch 8K TV every 60 seconds. (Imagine watching the Stanley Cup or Super Bowl on that sucker…)
Or, putting it another way, that’s the equivalent of $29,965.75 every second, or basically the average cost of buying a used car with current inflation (which has increased 28% since November 2020) every second.
Cyber Crime Statistics: A Look at the Most Common Cybercrime Methods & Tactics
In this next section of cyber crime statistics for 2021 and 2022, we’ll go over some of the most common attack methods and tactics that cybercriminals employed in studied cyber incidents.
6 — 36% of Data Breaches Involve Phishing in One Way or Another
Verizon’s 2021 Data Breach Investigations Report (DBIR) show that phishing was involved in nearly two in five data breaches. This is basically a 25% increase over the previous year’s dataset. This underscores the importance of providing phishing and general cyber awareness training to your employees (we’ll speak more on that later).
7 — Cybercriminals Targeted Web Apps in 80% of Hacking-Related Breaches
When it comes to the cause of hacking-related data breaches, insecure web apps tend to be a door that’s left wide open. Attackers love to search for weaknesses — unmitigated vulnerabilities such as unsanitized inputs and outdated software — they can exploit to gain access to other vulnerable resources and data within your IT environment. This is why Verizon’s 2021 DBIR data shows that four in five hacking-related breaches involve vulnerable web apps.
If you fail to protect your web apps, you’re essentially serving up your data to cybercriminals on a silver platter. By taking steps to make your web applications more secure against client- and server-side attacks as well as other exploits, you’ll better protect your data and network against their attacks and mitigate subsequent resulting breaches.
8 — 45% of Fraud Attacks Are Carried Out by Using Your Legitimate Brand as the Scapegoat
Just when you thought things couldn’t get any worse, it turns out there’s, apparently, a way to do just that. Research from Atlas VPN shows that almost half of the global fraud attacks that occurred in Q3 2021 involved brand abuse. Basically, this means cybercriminals communicate with targets via emails, social media, or other channels while impersonating major brands.
By doing this, attackers can simultaneously capitalize on your good name while dragging it through the mud by using it to trick or manipulate consumers. It’s a damaging criminal two-for-one special that leaves your organization the unwitting fall guy in this devastating scenario.
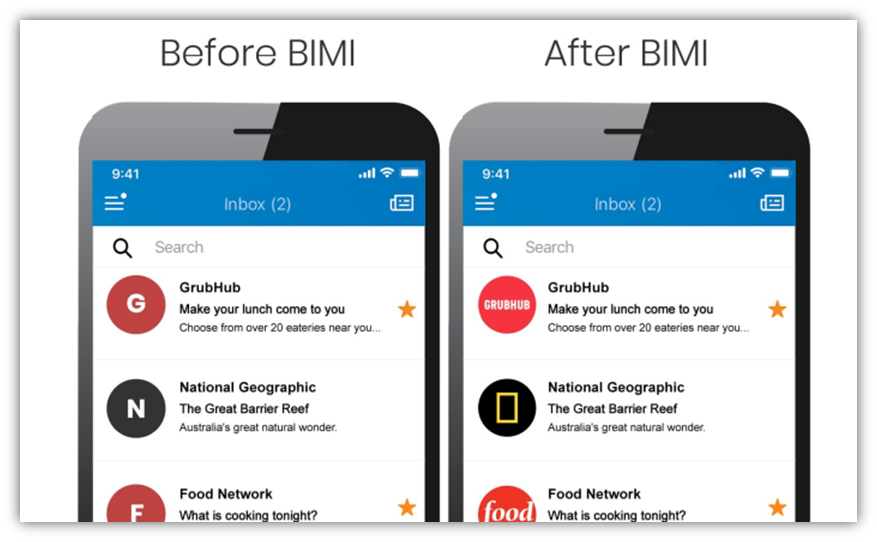
9 — DHL Takes the Undesirable Title as the #1 Impersonated Brand by Cybercriminals
According to Check Point Research’s Brand Phishing Report for Q4 2021, the delivery company takes on the mantle of the most commonly impersonated brands, surpassing the title’s usual contender Microsoft. In the last quarter of the year, DHL was represented in 23% of phishing attacks they studied globally. The other top five most commonly impersonated brands include:
- Microsoft (20%)
- WhatsApp (11%)
- Google (10%)
- LinkedIn (8%)
What would be really helpful to these companies would be implementing brand indicators of message identification (BIMI) and verified mark certificates (VMCs). Adding BIMI as part of your email outreach implementations helps recipients easily distinguish your legitimate emails from fake ones because your verified logo will appear in their inboxes. This means they won’t even have to click on the email (doing that opens them up to a slew of risk factors) to inspect it to try to figure out whether the email really came from you.
Using BIMI and a VMC also comes with the added benefit of helping you better visually brand your mail to your current and prospective customers.
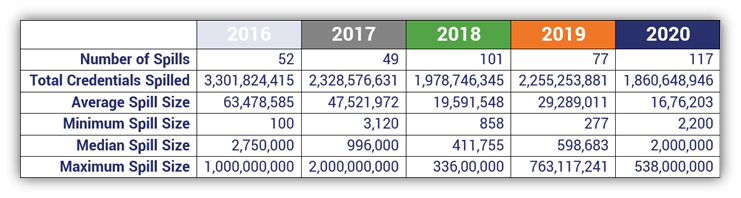
10 — 1.86 Billion Credentials Were Spilled in 2020
To quote F5 Labs: “There are two types of companies—those that acknowledge the threat of credential stuffing and those that will be its victims.” Their 2021 Credential Stuffing Report (published with Shape Security) shows that this type of login attack is a significant concern that isn’t going away. While the number of compromised credentials was lower in 2020 than 2019, the number of credential spills increased significantly:
Credential stuffing, which occurs when an attacker “stuffs” (enters) leaked or stolen login credential (email addresses/usernames and passwords) combinations into various login fields in an attempt to find a winning combination. Although this is sometimes recognized as a type of brute force attack, it’s different in that it’s using known leaked/stolen credentials instead of guessing one or both components.
Cyber Crime Statistics: How Companies Are Trying to Fight Back Against Cybercriminals
Whether it’s investing in new tools or hiring additional cyber security experts, companies globally are trying to find new ways to improve their defenses against individual and group threat actors. This cybercrime statistics section will cover several key considerations large organizations should consider.
11 — 72% of U.S. Businesses Rely on Hardware Security Modules (HSMs)
Here’s a nice statistic for us here in the United States — Entrust’s 2021 Global Encryption Trends Study data shows that we lead the way in terms of deploying HSMs, followed closely by Denmark (70%). Compare this to:
- United Kingdom (51%),
- France (45%), and
- Mexico (31%).
Hardware security modules are secure hardware components that you can use to protect your organization’s cryptographic keys, certificates, and passwords. Check out this article on HSMs (linked in the previous sentence) to learn more about these essential security solutions.
12 — 81% U.S. Organizations View HSMs As Key Components of Effective Encryption & Key Management
Following up on the last cybercrime statistic, Entrust’s 2021 report data also shows that U.S.-based survey respondents see these hardware-based security measures as “very important” and “important.” Comparatively, 65% of U.K. respondents and 58% of their French counterparts feel the same way.
13 — 91% of Organizations Want or Are Discussing Implementing PKI Automation
Public key infrastructure and digital certificates (SSL/TLS, client authentication, code signing, document signing, etc.) are integral to data security and integrity. DigiCert’s 2021 State of PKI Automation Report data shows that 9 in 10 organizations either want or are tossing around the idea of implementing PKI automation within their IT environments.
Rogue and shadow IT certificates and mismanagement issues are a serious concern considering that it only takes one expired certificate to bring down a world of pain on your organization and customers. A great example of this is the Equifax data breach of 2017. Since DigiCert’s survey also shows that organizations have an average of 50,000 certificates to manage, it’s no surprise that automating PKI processes would be on the table.
14 — 96% of Executives View PKI as “Essential to Zero Trust Architecture” (Even If They’re Not Currently Using It)
Data from Keyfactor’s 2021 Zero Trust PKI Survey shows that 9.6 out of 10 executives recognize public key infrastructure (PKI) as being central to a zero trust strategy. Zero trust architecture is an approach that’s been picking up a lot of traction over the last few years. It’s a concept in which no users, internal or external, are automatically trusted and must undergo continuous authentication to ensure that they are who they say they are.
However, their survey also shows that a whopping 61% — nearly two-thirds of respondents — don’t include zero trust within their zero trust strategies. So, this is another example of organizational leaders knowing what they should do even if they choose to not do so.
… We’ve gotta do better, guys. Cyber attacks and data breaches aren’t going away and only continue to increase with each passing year. It’s high time for leaders to prioritize PKI and data security by dedicating the money, personnel, and other resources to doing what needs to be done. Speaking of which…
15 — 82% of Organizations Say Their IT Security Budgets Have Increased (But By How Much?)
Accenture’s 2021 State of Cyber Resilience Report shows that there’s a growing commitment among organizations to increase their IT budgets. But the question that remains is: how much are these budgets growing? Considering that the average organization’s IT security budget still only constitutes 15% of the overall IT budget, it’s not the rate of speed we’re hoping to see.
Cyber security threats and incidents are increasing by the day — businesses need to have the tools and resources in place to face them head-on and prevent them from occurring in the first place.
16 — 9 in 10 Finance Industry Organizations’ Employees Receive Awareness Training
Data from Verizon’s 2021 Data Breach Investigations Report (DBIR) shows that 85% of breaches involved the “human element” — meaning that either your employees were targeted or they made a mistake that resulted in a breach. Either way, one of the best solutions to this problem is to train your employees.
Cyber awareness training helps them learn to recognize and safely respond to suspected threats and attacks so they know what to do when things go wrong (which, inevitably, they will). So, I’m glad to see that KnowBe4’s 2021 State of Privacy and Security Awareness Report shows that 91% of employees within the Finance industry shared that they’d undergone at least one form of related training.
Cyber Crime Statistics: How Cyber Security Measures Positively Affect Your Organization (and You)
Cyber security measures are crucial for combatting cyber attacks and mitigating data losses; they also contribute to minimizing the costs associated with these security incidents. Cyber security measures include everything from using network security tools and encryption to protect your sensitive data and systems to using artificial intelligence (AI) and zero-trust to make access to your systems more secure.
Let’s explore some of the ways having a mature security posture impacts cyber crime rates and associated costs in this next set of cybercrime statistics.
17 — Breach Costs for Companies Using Strong Encryption Cost $1.25 Million Less on Average
IBM’s Cost of a Data Breach 2021 data shows that organizations that relied on no encryption or weak encryption wound up paying an average of 29.4% more per breach. That’s because the average cost of a breach involving an organization using high standard encryption (i.e., at least AES 256-bit encryption) cost $3.62 million, whereas a breach that didn’t cost an average of $4.87 million.
18 — Having a Mature Zero-Trust Architecture Decreases Average Breach Costs by $1.76 Million
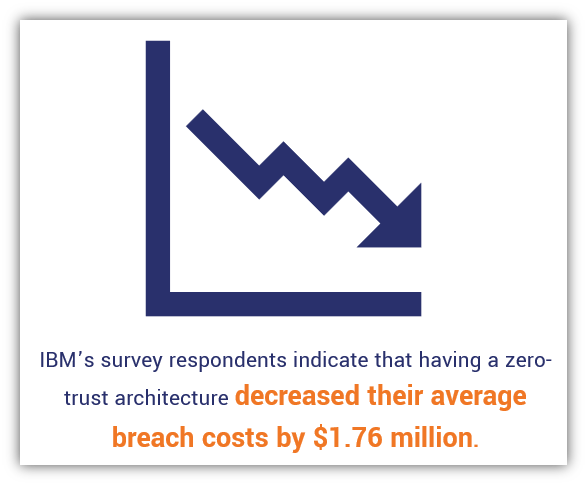
Earlier in the article, we talked about the importance of adopting a zero trust approach to cyber security. The same IBM report further substantiates this concept, stating that the average cost of a breach was $1.76 million less at organizations with a mature zero trust approach than those that lacked it.
19 — 30% of CISOs’ Roles Will Be Directly Measured By the Value They Bring to the Business
Here’s a bit of a different approach that having strong cyber security can benefit you in addition to your organization. If you’re a chief information security officer, Gartner estimates that nearly one-third of your value is measured by your effectiveness at bringing value to the organization you work for.
CISOs have an often-thankless job — if you do 99.9% of things right but have one mistake leads to a breach, that’s the one thing you’ll be remembered for.
Cyber Crime Statistics: The Most Common Cyber Crime Prevention Challenges
In this last section on cybercrime statistics for 2021 and 2022, we’ll go over some of the biggest hang ups organizations face when it comes to keeping cybercriminals at bay.
20— A Lack of Cyber Awareness is #1 Barrier to Establishing a Strong IT Security Defense
CyberEdge Group’s 2021 Cyberthreat Defense Report shows that “low security awareness among employees” continues to rank as the leading challenge. This issue has ranked among the top barriers for many years, but it’s the second year in a row that’s been ranked as the top inhibition.
21 — One of the Top 5 Risk Factors for Organizations: Not Training Your Employees
One of the most glaring risk factors for organizations is not training your employees regarding regulations, laws, and mandates, according to Proofpoint’s 2022 Cost of Insider Threats Global Report. If they don’t know what requirements exist, how can they abide by them when doing their jobs each day?
Of course, this same concept also applies to not training your employees on cyber security best practices and phishing awareness; if they don’t know how to recognize or respond to a suspected threat, they’re likely to fall for them.
22 — 65% of Companies View Not Knowing Where Data Is as the Biggest Challenge
Entrust’s 2021 Global Encryption Trends Study data shows that keeping tabs on all sensitive data is the leading challenge for businesses when it comes to employing encryption. This makes sense considering that you can’t encrypt data if you don’t know where it’s located or how much of it exists.
23 — 40% of Companies Use Spreadsheets to Manually Track PKI Digital Certificates
Another concern regarding knowing where stuff is located relates to your organization’s digital certificates. These small data files are incredibly important and are serve as your organization’s digital identity. When you mismanage or lose your certificates, it’s like being careless with your driver’s license or passport and how losing that can quickly cause many problems.
Keyactor shares in their 2021 State of Machine Identity Management report that two in 5 organizations use spreadsheets to manage these certificates. Doing this is troublesome considering that large organizations can have tens of thousands — or hundreds of thousands — of digital certificates within their IT environments.
If one of those expires, it can cause downtime or leave any data transmitted to and from that site at risk of compromise and/or theft. This is because you’ve essentially allowed your HTTPS protection to lapse by not replacing your certificate before it expired.
it’s easy to see why having an efficient certificate management tool at your disposal is essential when you consider:
- 81% of surveyed organizations report having experienced one or more certificate outages in the previous year, and
- 41% experienced four or more certificate outages within the same time period. Yikes.
Final Thoughts on Cybercrime Statistics in 2022
Congrats on making it the whole way through this article — we know it’s a lot to unpack. However, each of these cybercrime statistics provides valuable insight into what attackers are doing and things you can consider for improving your organization’s cyber defenses.
The truth is that no matter what you do, there’s always going to be a cybercriminal who is trying to find ways to outsmart and outmaneuver you. The best thing you can hope for is to take steps to make your organization and data as secure as possible by:
- Implementing strong cyber security policies and procedures,
- Ensuring you have the right people (with the right skills) and tools in place,
- Dedicating the money and resources to securing your network, devices and applications, and
- Using encryption to keep your data secure both in rest and in transit.
[ad_2]
Article link
